There are two types of banner grabbing.

Banner grabbing attack concept.
One of these lesser known methods is known as banner grabbing and in this article we shall divulge all the facts you need to know about it and also how you can protect yourself against such attacks.
Banner grabbing is an activity that is used to determine information about services that are being run on a remote computerthis technique can be useful to administrators in cataloging their systems and ethical hackers can also use it during penetration tests.
This banner information might give a hacker the leg up because it may identify the operating system the version number and the specific service packs to give the bad guys a leg up on attacking the network.
Banners are intended for network administration.
Banner grabbing and operating system identificationwhich can also be defined as fingerprinting the tcpip stackis the fourth step in the ceh scanning methodologythe process of fingerprinting allows the hacker to identify particularly vulnerable or high value targets on the network.
Related searches to server hacking what is banner grabbing.
If the system is not well configured it may leak information about itself such as the server version phpaspnet.
Banner grabbing or active reconnaissance is a type of attack during which the attackers send requests to the system they are attempting to attack in order to gather more information about it.
Banner grabbing is essentially a practice that is used to obtain information about services that are being run on a remote computer or client.
An attacker can make use of banner grabbing in order to discover network hosts and running services with their versions on their open ports and moreover operating systems so that he can exploit it.
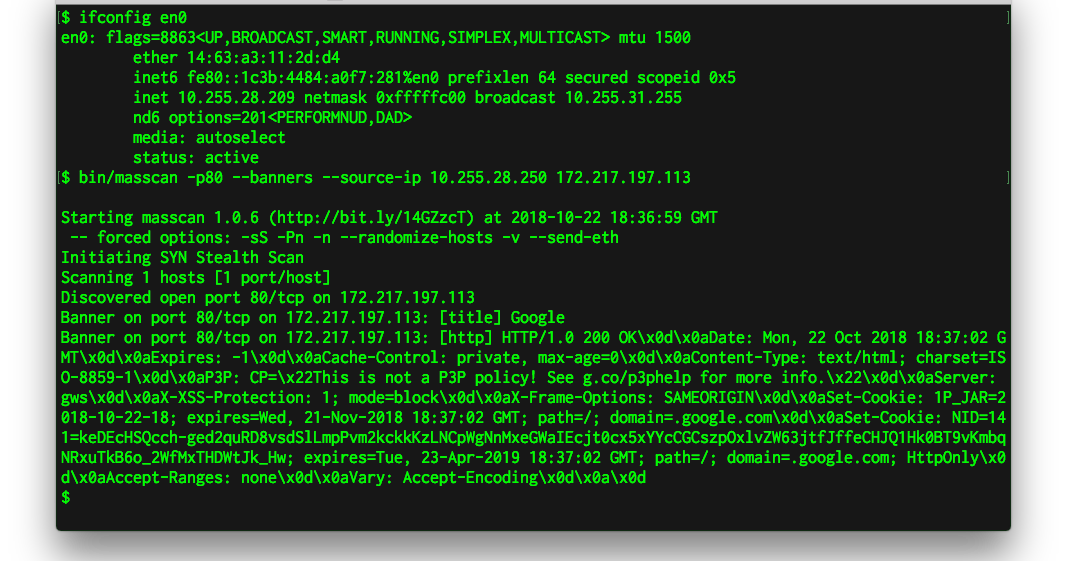
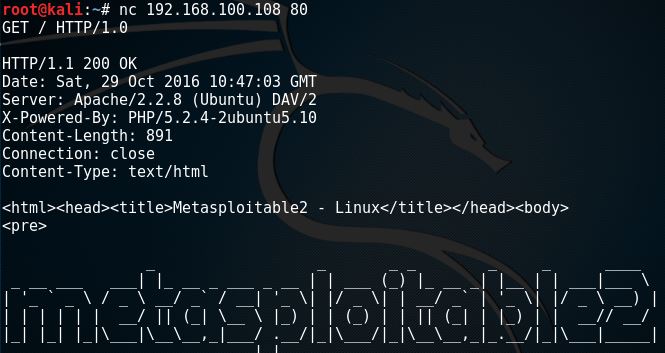
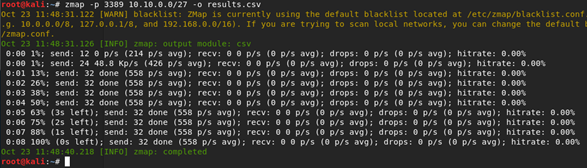
Tools commonly used to perform banner grabbing are telnet nmap zmap and netcat.
You can grab banners by using good old telnet or tools such as nmap and superscan.
Banners usually contain information about a service such as the version number.
Banner grabbing is the act of capturing the information provided by banners configurable text based welcome screens from network hosts that generally display system information.
Some examples of service ports used for banner grabbing are those used by hyper text transfer protocol file transfer protocol and simple mail transfer protocol.
Banner grabbing or os fingerprinting is the method to determine the operating system running on a remote target system.
Identifying the os used on the target host allows an attacker to figure out the vulnerabilities the system posses and the exploits that might work on a system to.
Ports 80 21 and 25 respectively.

Bp1esjy5rys4im

Attack Overview Youtube

Reports Publications

Pdf Network Security Assessment Using Internal Network
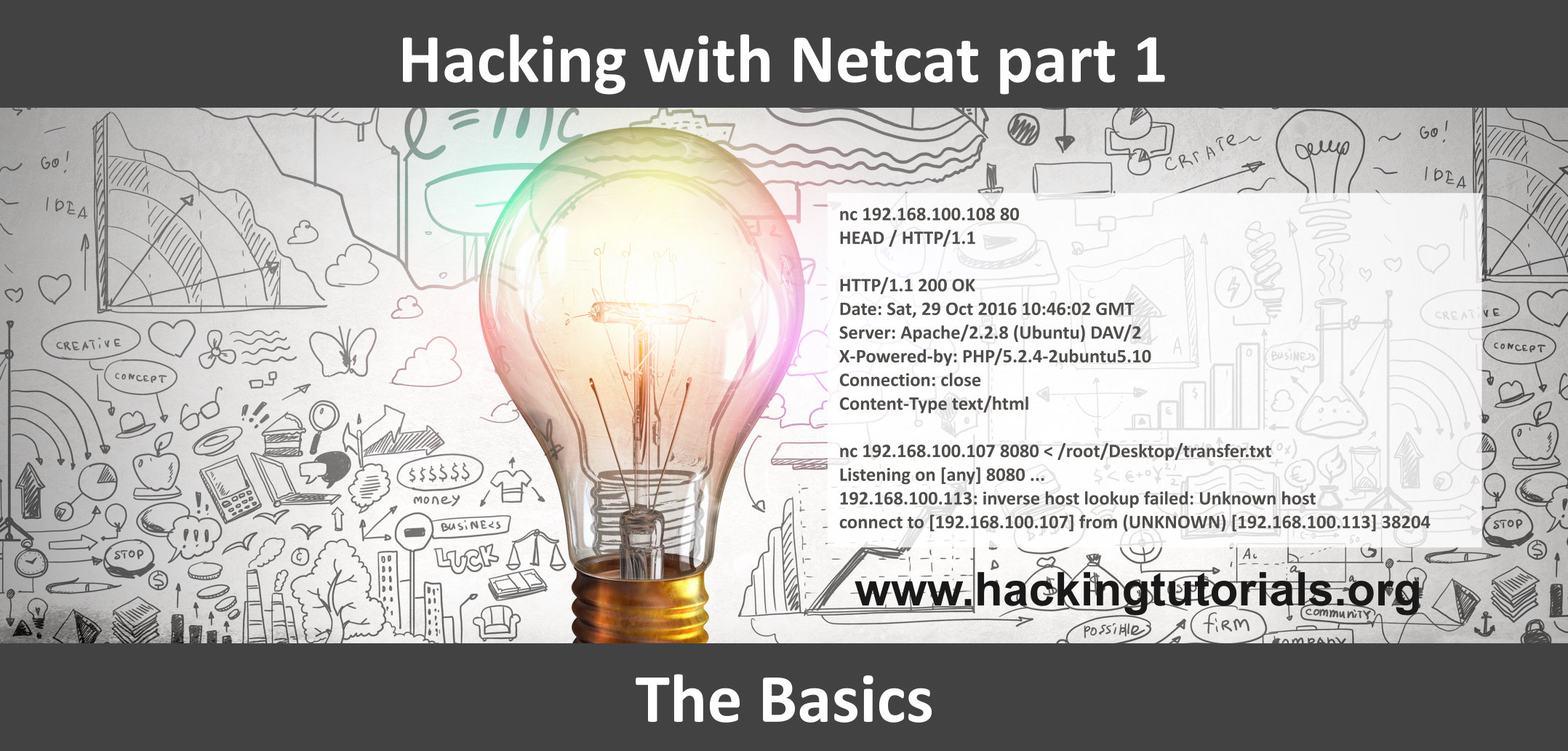
Hacking With Netcat Part 1 The Basics Hacking Tutorials

Hacking Web Server Defiana Arnaldy M Si Ppt Download

Internet Organised Crime Threat Assessment 2018 Europol
Security And Attack Vector Analysis Of Iot Devices Springerlink

Learn Web Application Penetration Testing Noteworthy The

Dk8xepsdnnzadm

A Very Incomplete Diagram Of Network Attacks Pdf Free Download

Hacking Exposed Windows Microsoft Windows Security Secrets And

Attacking The Ftp Service Penetration Testing Lab
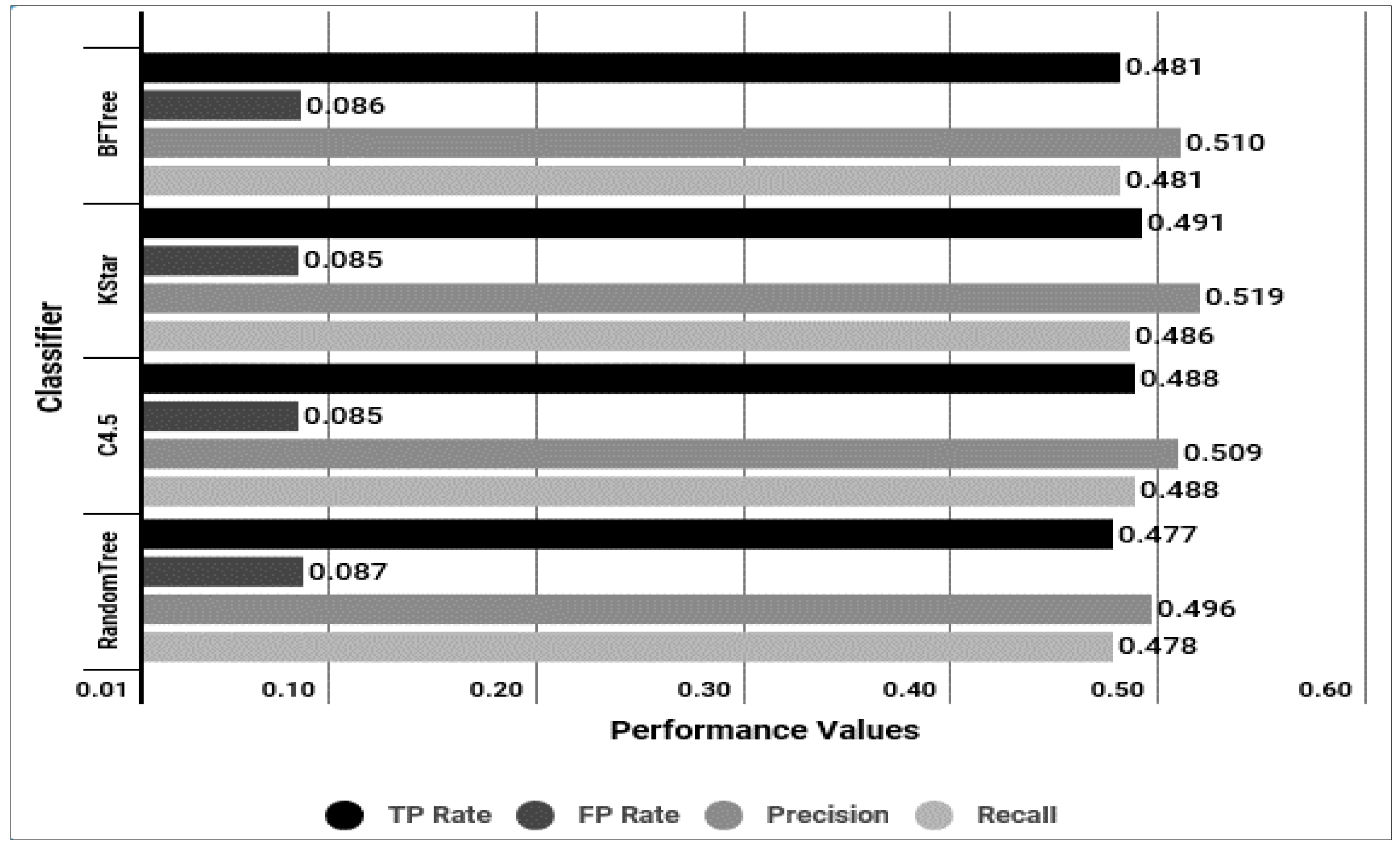
Symmetry Free Full Text An Intelligent Improvement Of Internet

Module 3 Scanning

Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 682 8622 Rep Rep1 Type Pdf

Risk Management And Vulnerabilities Algosec
The Three Most Effective And Dangerous Cyberattacks To Azure And

Hacking And Your Cybersecurity Future

Https Ieeexplore Ieee Org Iel7 8169968 8227816 08228241 Pdf

Case Study Mitigating Browser Extension Attacks Jscrambler Blog

A Step By Step Guide To Vulnerability Assessment

Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 682 8622 Rep Rep1 Type Pdf

08092019 Xenophobic Attacks Presidency Rejects S African
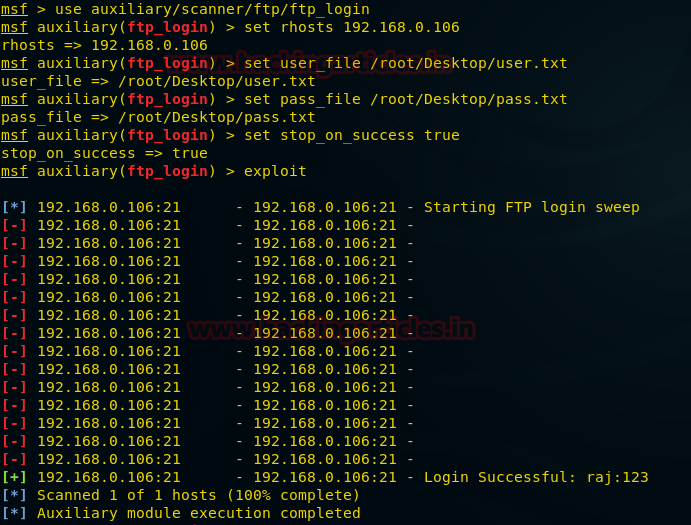
Penetration Testing Of An Ftp Server Shahmeer Amir

A Complete Guide To Nmap Nmap Tutorial Edureka

Dr Hacker Isn T Wearing A White Coat Secplicity Security

Attack Surface Concept Types Tools And Reduction Strategies

Malvertising Campaign

Certified Ethical Hacker Ceh Nc Expert

Hacker Attack Laptop Computer Background Icon Binary Shield And

5 Amazing Ethical Hacking Techniques

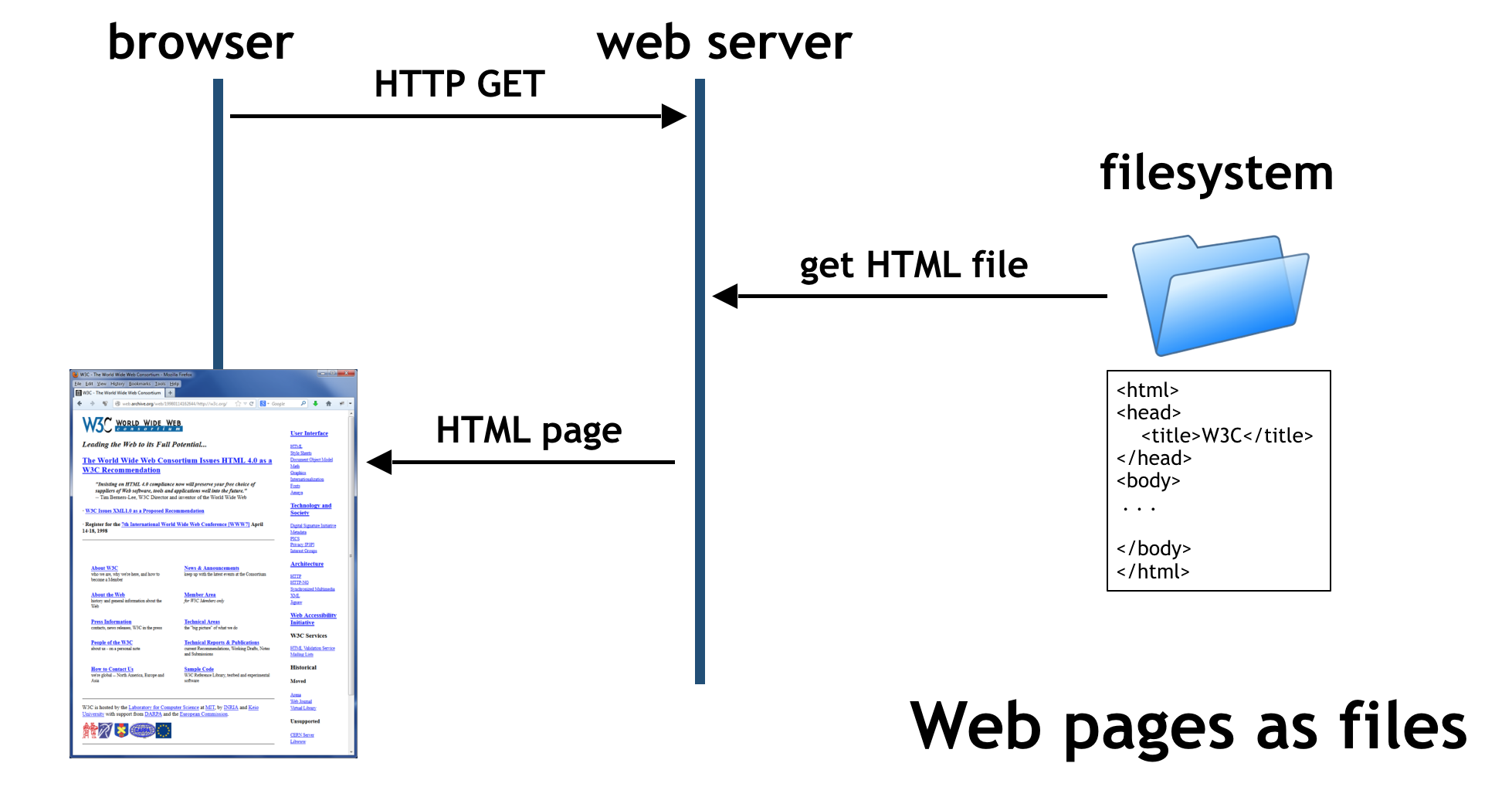
How Web Servers Work Web Servers Use Hyper Text Transfer Protocol

Banner Grabbing Penetration Testing

Pdf Text Advertising Blindness The New Banner Blindness

Ddos Goes Mainstream How Headline Grabbing Attacks Could Make

How An Attack On A Company You Ve Never Heard Of Shut Down The

What Is A Banner Grabbing Attack 3 Ways To Protect Yourself

Ceh Training In Hyderabad Certified Ethical Hacking Training

A Very Incomplete Diagram Of Network Attacks Pdf Free Download

Imagenes Fotos De Stock Y Vectores Sobre Malware Infografia

Banner Grabbing Get Certified Get Ahead
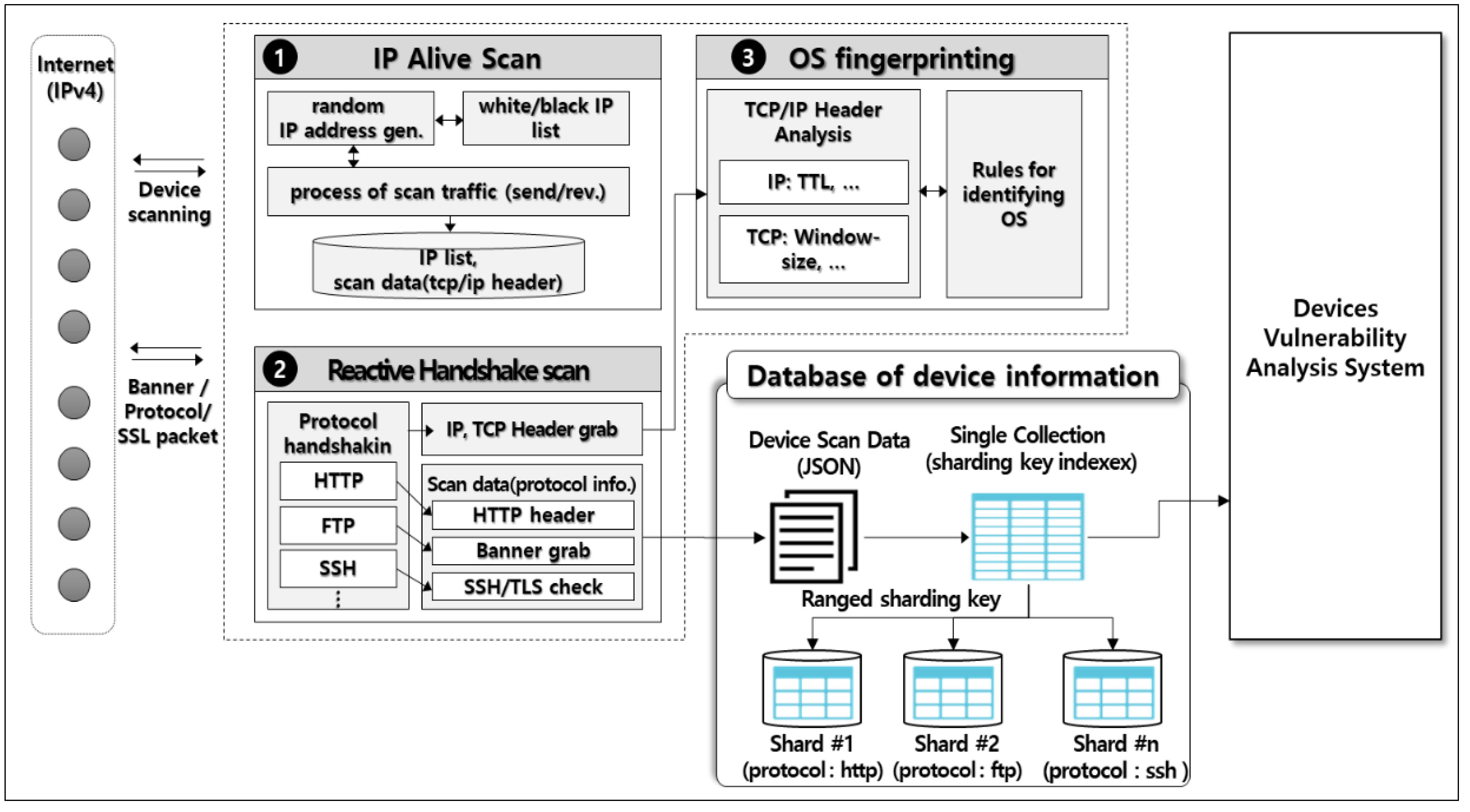
Symmetry Free Full Text An Intelligent Improvement Of Internet

Certified Ethical Hacker Ceh Complete Video Course And Practice

Attack On Saudi Oil Sites Raises Risks Times Leader

Https Www Sans Org Cyber Security Summit Archives File Summit Archive 1510711505 Pdf
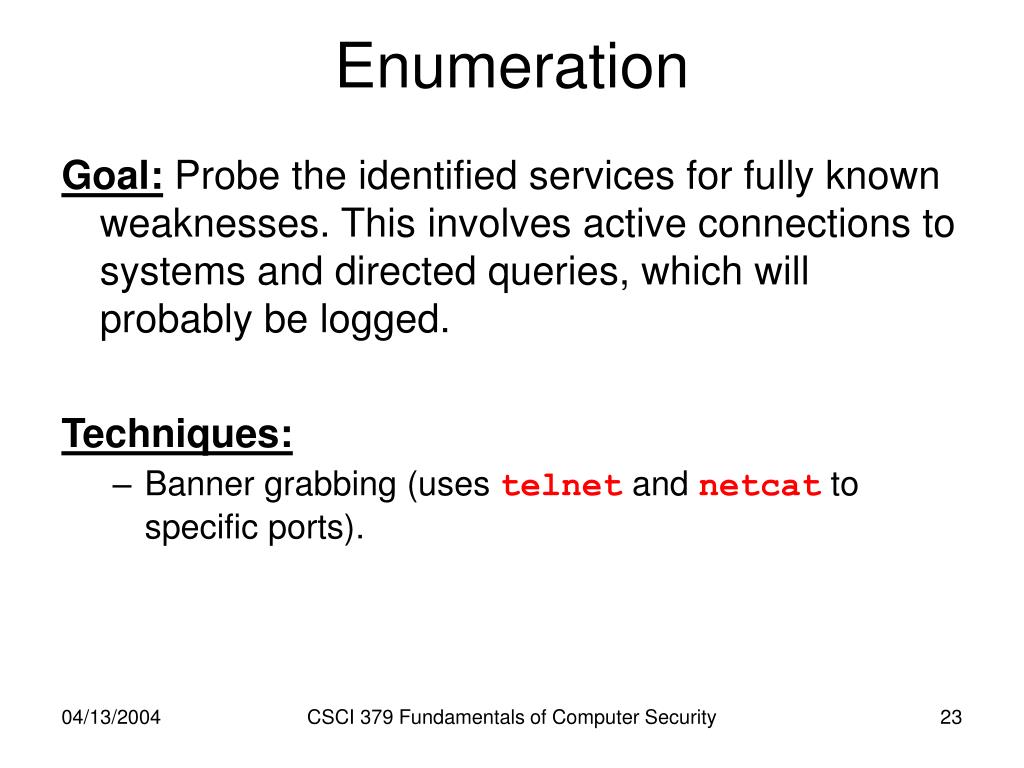
Ppt Fundamentals Of Computer Security Powerpoint Presentation

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Top Ethical Hacking Online Course Certified Ethical Hacker Ceh

Preventing Web Attacks With Apache Informit

Https Www Blackhat Com Docs Us 17 Thursday Us 17 Mittal Evading Microsoftata For Activedirectory Domination Pdf

File000140
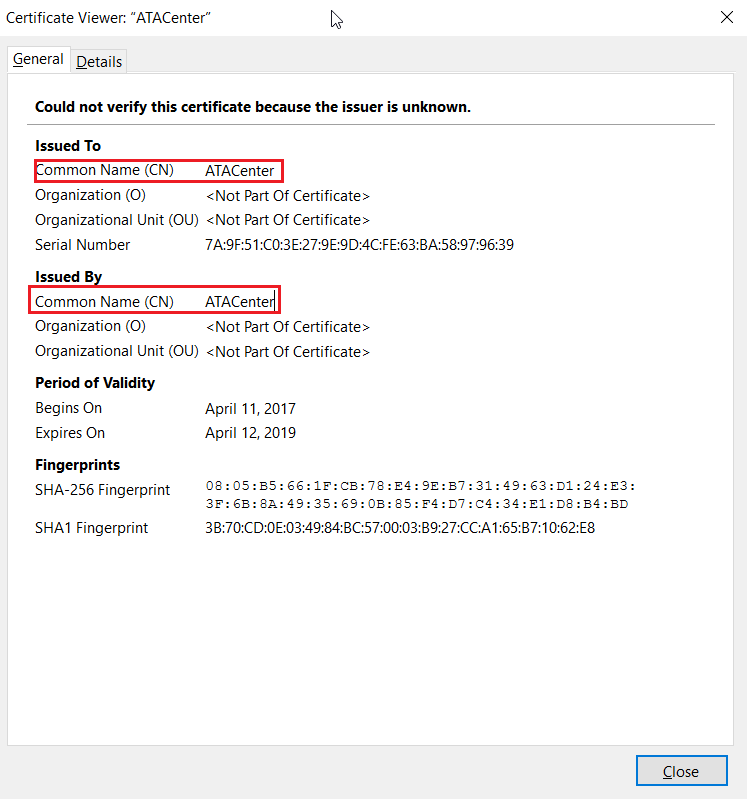
Lab Of A Penetration Tester Week Of Evading Microsoft Ata Day 5

Imagenes Fotos De Stock Y Vectores Sobre Malware Infografia

Attacking The Ftp Service Penetration Testing Lab

40 Cyber Security Mcq With Answers And Explanations Yeah Hub

Nmap Tutorial Common Commands Network Computing

What Is A Banner Grabbing Attack 3 Ways To Protect Yourself

What Is A Banner Grabbing Attack 3 Ways To Protect Yourself

Be Careful Where You Point To The Dangers Of Stale Dns Records
Hacking And Your Cybersecurity Future

Certified Ethical Hacker Ceh V10 Ec Council Iclass

All Time Best Ethical Hacking Books Hacking Lab Setup Video

Lab Of A Penetration Tester Week Of Evading Microsoft Ata Day 5
Errata Security Masscan As A Lesson In Tcp Ip

Hand Reaching From The Dark And Grabbing Or Attacking Concept

Certified Ethical Hacker Ceh Version 9 Cert Guide 2nd Edition

Certified Ethical Hacker Ceh V10 Ipspecialist
Hacking With Netcat Part 1 The Basics Hacking Tutorials

Amazon Com Under Night In Birth Exe Late Cl R Playstation 4
The Three Most Effective And Dangerous Cyberattacks To Azure And

Certified Ethical Hacker Practical C Eh Practical Ec Council
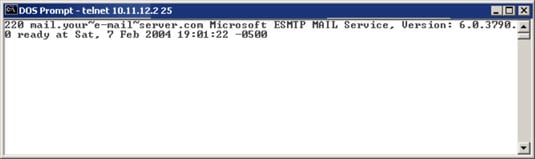
How Hackers Grab Banners To Penetrate Your Network Dummies

Configuring Your Web Server To Not Disclose Its Identity Acunetix

Port Scanning And Super Scan 4 1

Net Cat Konda S Security Website

Banner Grabbing Penetration Testing

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Ptes Technical Guidelines The Penetration Testing Execution Standard

Top 20 Honeypots To Detect Network Threats

Https D3alc7xa4w7z55 Cloudfront Net Static Upload 201 0123 2016 Ossovernet Ethical Hacking Pdf

Detect Sqli Attacks In Web Apps Using Nvs By Ijcseitjournal Issuu

Migraine Attack Stock Illustrations 181 Migraine Attack Stock

Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 682 8622 Rep Rep1 Type Pdf

Hands Grabbing On Chest Copy Space On Right For Heart Attack

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Cyber Security Certification Course Tickets By 3g Irps Iit Madras

Certified Ethical Hacker Ceh Complete Video Course And Practice

Https Ieeexplore Ieee Org Iel7 8169968 8227816 08228241 Pdf

Network Sockets Python Penetration Testing Essentials Second

Canonicalization Attack Updated 2019

What Is Banner Grabbing Best Tools And Techniques Explained

Detect Sqli Attacks In Web Apps Using Nvs By Ijcseitjournal Issuu

The Cyber Security Glossary For Safe Online Experiences

What Are The Phases Or Penetration Testing Of A Website Or Web

Ynwxhexvy2zbam

Scanning Attack An Overview Sciencedirect Topics

Poltergeist 1982 Film Wikipedia























































































