Este concepto se refiere a.

Banner grabbing cwe.
Obecnie cewe dziala w 24 krajach zatrudnia ponad 3 500 osob i dysponuje 12 laboratoriami fotograficznymi.
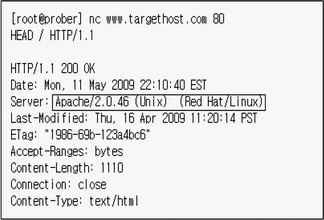
Uno de los aspectos a la hora de realizar controles sobre una aplicacion web es la informacion que puede obtenerse a traves de lo que se conoce como banner grabbing.
Wir bieten 3 verschiedene individuelle bannerarten an um ihren bedurfnissen gerecht zu werden.
Grundsatzlich erfullen die stoffbanner materialien bei cewe printde hochste anspruche in sachen farbbrillanz und strapazierbarkeit im detail unterscheiden sie sich aber je nachdem welche anspruche sie an das banner stellen.
Sie haben die.
Lets explore the different types of banner grabbing techniques.
Keine uploadgebuhren oder mindestbestellmengen.
The phrase information disclosure is also used frequently in policies and legal documents but do not refer to disclosure of security relevant information.
Die cewe bestellsoftware macht das designen einfach und leitet sie schritt fur schritt durch die gestaltung.
W skali roku cewe drukuje miliardy fotografii miliony cewe fotoksiazek oraz mnostwo fotoprezentow kazdy produkt tworza nasi klienci wedlug swojego pomyslu a my dbamy o idealny efekt koncowy.
Art prints eignen sich ideal als geschenk in der passenden geschenkbox oder als ganz personliche erinnerung die mehr als nur ein foto ist.
Mit ihrem l banner kommt ihr firmenlogo ihr werbeslogan und ihr werbemotiv kraftig und leuchtend zur geltung.
Personliche fotoprodukte gestalten und erstellen bei cewe wir machen mehr aus ihren fotos cewe fotoservice jetzt entdecken.
Cewe printde liefert eine transporttasche mit in der sie ihr banner lagern und mobil mitnehmen konnen.
Erstellen sie minutenschnell individuelle werbebanner.
Unsere individuellen vinylbanner sind in 9 verschiedenen grossen verfugbar und ideal dazu geeignet fur ihr unternehmen oder event zu werben.
This term is frequently used in vulnerability databases and other sources however disclosure does not always have security implications.
Banner grabbing is a technique used to gain information about a computer system on a network and the services running on its open ports.
So sind sie auf jedem event das gesprachsthema und bauen eine beziehung zu ihren besuchern und kunden auf.
Administrators can use this to take inventory of the systems and services on their network.
Polyester gewebe ist besonders kraftig abwisch und strapazierbar.

Unknown Number Of Bluetooth Le Devices Impacted By Sweyntooth

Sd143 Febmar2015 Web By James Hirst Issuu

Lotus Domino Penetration Through The Controller

Https Media Blackhat Com Bh Eu 12 Sintsov Bh Eu 12 Sintsov Lotus Domino Slides Pdf

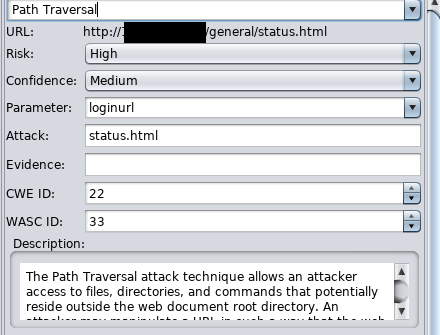
Information Disclosure Attacks In Web Applications Netsparker

English Articles40

Unknown Number Of Bluetooth Le Devices Impacted By Sweyntooth

Https Media Blackhat Com Bh Eu 12 Sintsov Bh Eu 12 Sintsov Lotus Domino Slides Pdf

Comparison Of Penetration Testing Tools For Web Applications Pdf
Vulnerability Reports Consolidation For Network Scanners

Https Webthesis Biblio Polito It 6422 1 Tesi Pdf

Information Disclosure Attacks In Web Applications Netsparker

Tenable Blog

Security Audit Report Pdf Free Download

Https Www Filepicker Io Api File 7sty2pavqbe3hoj4oryx

Pdf Jefferson Davis And Proslavery Visions Of Empire In The Far

Top 10 Cwe By The Number Of Cves Download Table

Https Www Inforsec Org Wp Wp Content Uploads 2019 01 Session3 E4 B8 B0 E8 Bd A9se18 Slides Final43 Pdf

Vulnerability Assessments Risk Threats

Ssrf I Break Software

D Link Security Restriction Bypass

Frozen 2 Elsa X Fem Reader T W O Wattpad

Metasploit The Penetration Testers Guide By Sandra Sopian Issuu

Top 10 Cwe By The Number Of Cves Download Table

Security

Metasploit Tutorial 1 Pages 51 100 Text Version Fliphtml5
A Study On The Service Identification Of Internet Connected

Frustration Over Crime Pushes City Resident To Post Sign Warning

Iis Response Cache

Top 10 Cwe By The Number Of Cves Download Table

Owasp Testing Guide V4 By Janaksinh Jadeja Issuu

Security

We Ain T Never Getting Older Vince X Darren Six Wattpad

Github Tracehowler Bible Eh Bble

Pole Advertising Services Lamp Pole Kiosk Advertising

Personal Information Disclosure

Top 10 Cwe By The Number Of Cves Download Table

Northampton Town 4 Crewe Alex 1 Recap Poor Defending Is Punished

Https Webthesis Biblio Polito It 6422 1 Tesi Pdf

Https Www Filepicker Io Api File 7sty2pavqbe3hoj4oryx

Https Docs Tenable Com Nessus 8 7 Content Resources Pdf Nessus 8 7 Pdf

Ceh Exam Final 1 Docx Transmission Control Protocol Port

2kkuu7ita

World S Best Cheeses Completes Cwi Asset Acquisition Number Of

Top 10 Cwe By The Number Of Cves Download Table

Group Of Mothers Running With Baby Strollers In California Picture
A Study On The Service Identification Of Internet Connected

Https Media Blackhat Com Bh Eu 12 Sintsov Bh Eu 12 Sintsov Lotus Domino Slides Pdf

Vulnerability Information Disclosure

Blue Banner V2 Spring 2007 By Smcs Advancement Issuu

Nist Sp 800 115 Technical Guide To Information Security Testing

Top 10 Cwe By The Number Of Cves Download Table

Sql Injection Attacks And Defense 2009

Information Disclosure Icon
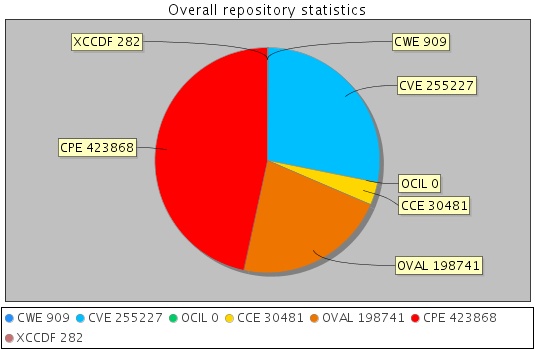
Secpod Scap Repo A Repository Of Scap Content Cve Cce Cpe Cwe

Brazilian Women Protest Legislation That Could Ban Abortion

Https Media Blackhat Com Bh Eu 12 Sintsov Bh Eu 12 Sintsov Lotus Domino Slides Pdf

Cht Exploit Google Docs Xspa Ssrf

Hallmark Valentines Day Cards Pack Heart 6 Valentine Cards With

Cybersecurity Initiatives

English Articles39

Lotus Domino Penetration Through The Controller

Ceh Exam Final 1 Docx Transmission Control Protocol Port

Vuldb Splunk App 2 0 Showcase Digitalmunition

Https Www Mdpi Com 1424 8220 19 15 3380 Pdf
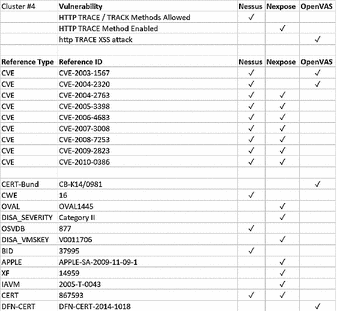
Vulnerability Reports Consolidation For Network Scanners

Blue Banner V2 Spring 2007 By Smcs Advancement Issuu

Let Cbk Reopen Chase Bank Asap Daily Nation

Https Www Filepicker Io Api File 7sty2pavqbe3hoj4oryx
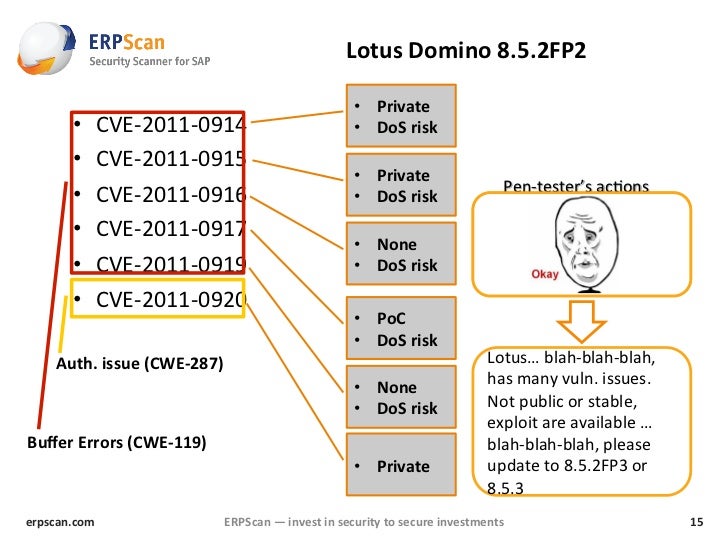
Lotus Domino Penetration Through The Controller
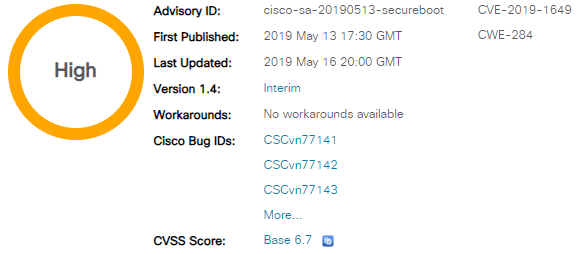
My Personal Cyberblog Content Of 2019 Sorted By Week

Iis Response Cache

Fallscountanywhere Instagram Posts Gramho Com

Pdf Profesional Penetrationa Hương đao Anh Academia Edu

Comparison Of Penetration Testing Tools For Web Applications Pdf

Bctgi

Https Repo Zenk Security Com Techniques 20d Attaques 20 20 20 20failles Lotus 20domino 20penetration 20through 20the 20controller Pdf

Q3 2018 Threat Report
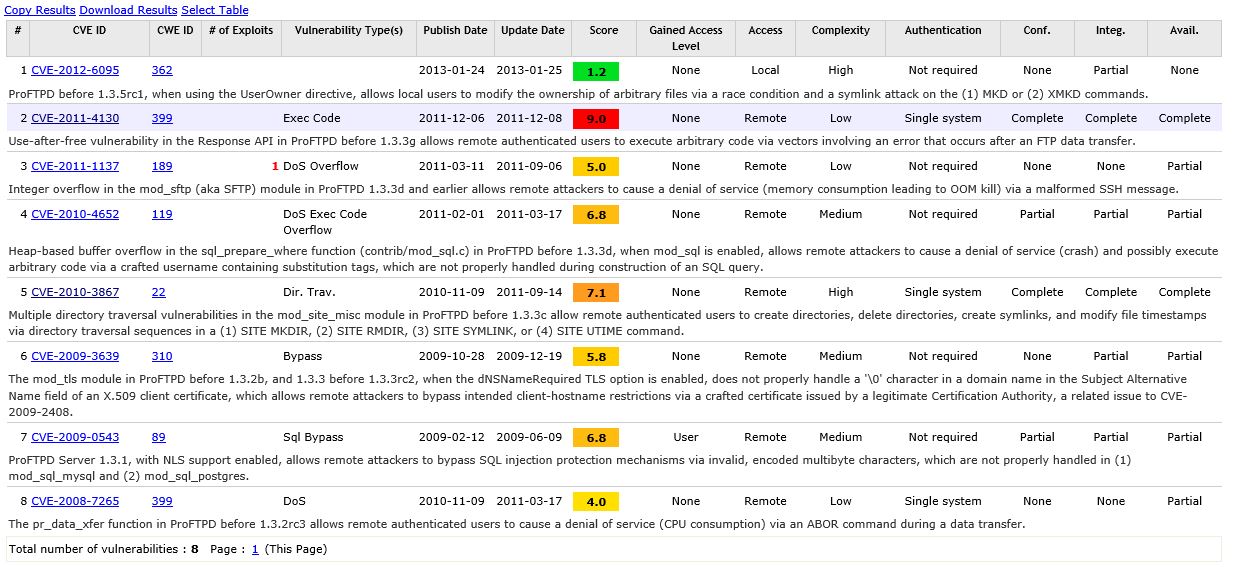
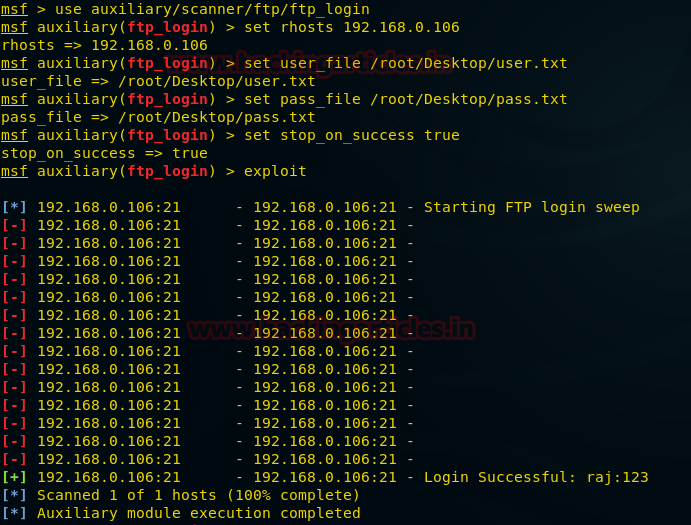
Metasploitable 2 Vulnerability Assessment Crackware
Nk9y8bzi7vg1zm

Lotus Domino Penetration Through The Controller

Ssrf I Break Software

Content Creation Process How To Create Outstanding Content In

Https Www Filepicker Io Api File 7sty2pavqbe3hoj4oryx

What Is Banner Grabbing Best Tools And Techniques Explained

Disclose

Abc7 News 5 00am Kgo October 9 2019 5 00am 5 58am Pdt Free

Https Www Filepicker Io Api File 7sty2pavqbe3hoj4oryx
Riding The Printer Pwnie By

Top 10 Cwe By The Number Of Cves Download Table

Navigating Mobile World Congress 2017 A Comprehensive Daily Guide

Nova Stranka 2

Top 30 Bank Exam Coaching Centre In Lodhar Best Bank Exam

Crewe Alex 1 Barnsley 3 Recap How It Happened Cheshire Live

Https Repo Zenk Security Com Techniques 20d Attaques 20 20 20 20failles Lotus 20domino 20penetration 20through 20the 20controller Pdf

Jufltgbw7hmrdm
Penetration Testing Of An Ftp Server Shahmeer Amir
Who Controls The Vocabulary Controls The Knowledge Fbc S













































































