
Best Tools For Red And Blue Teams Are Methodology Experience

Cyber Security And Ethical Hacking Mcq With Answers Part 4

Banner Grabbing

10 Tools You Will Use In Hacking Alpha Cyber Security

3ay4pwz5myk42m

5 Ways To Banner Grabbing

Cyber Security Financial Advisers

Iipzuog9quj5lm
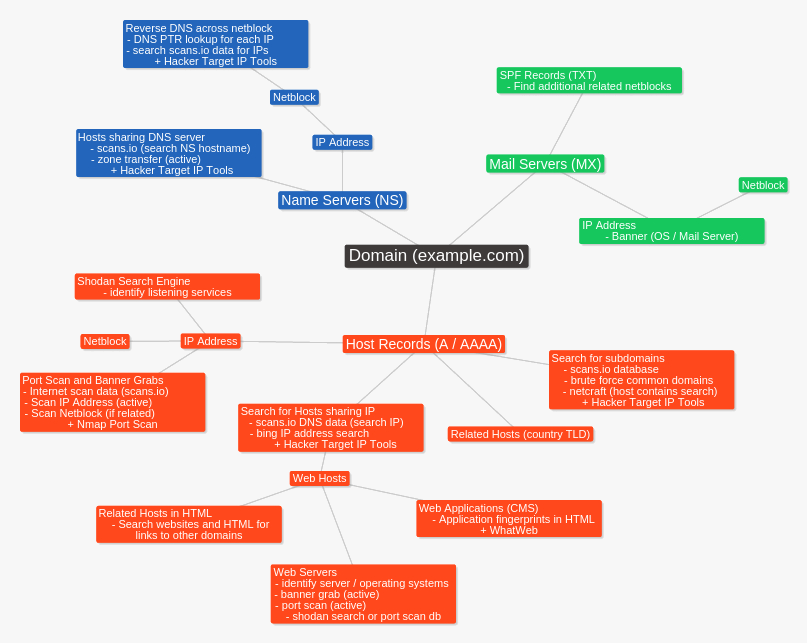
Quietly Mapping The Network Attack Surface

Rmar Certified Cyber Security Expert Rccse Information Age

Tips On Protection Against Phishing Scam Cyber Security

Information Disclosure Attacks In Web Applications Netsparker

Banner Grabbing With Cmd Demo Youtube

Ethical Hacking Summer Training In Jaipur

Pdf Online Assessment For Hands On Cyber Security Training In A

Banner Grab Food

Top 10 Reasons To Pursue The Certified Ethical Hacker When

Cyber Security Today Be Careful Buying Connected Gifts For

The State Of Cybersecurity Today Avast

Top 10 Most Common Types Of Cyber Attacks

10 Tools You Will Use In Hacking Alpha Cyber Security
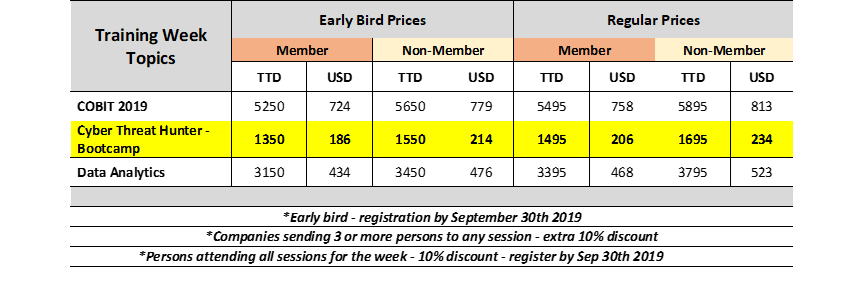
Cyber Threat Hunter Bootcamp Trinidad Tobago Chapter
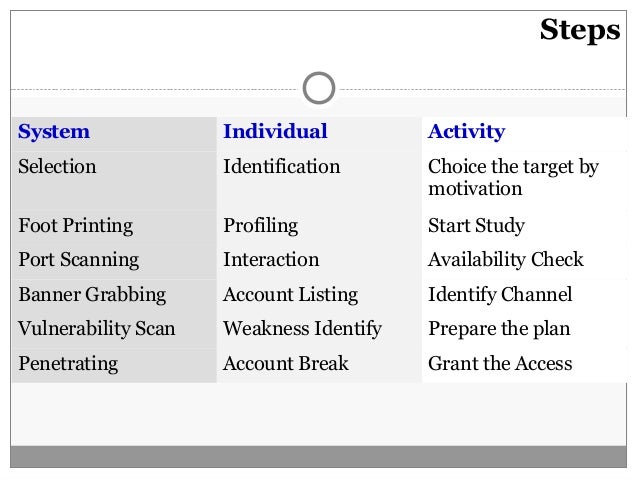
Cyber Security Awareness File 1 Of 2

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Banner Grabbing Cybersecurity Glossary
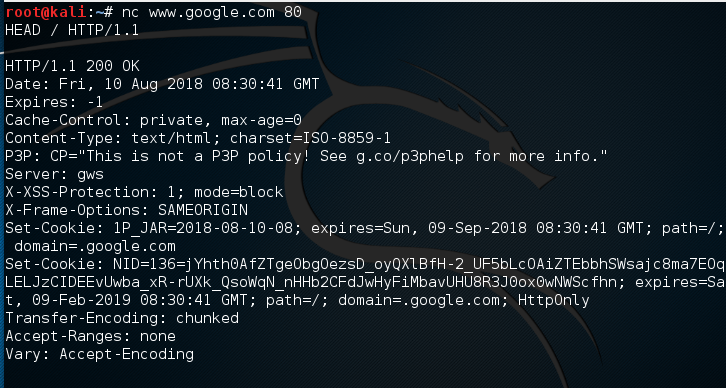
Understanding Netcat The Swiss Army Knife For Ethical Hacking

Eliminate Banner Grabbing In Apache Tomcat

Web Server And Its Types Of Attacks Ethical Hacking

What Is Banner Grabbing Best Tools And Techniques Explained

Pin On Computer

Penetration Testing Services In Dubai Penetration Testing In Dubai

Hacker Attack Laptop Computer Background Icon Binary Shield And
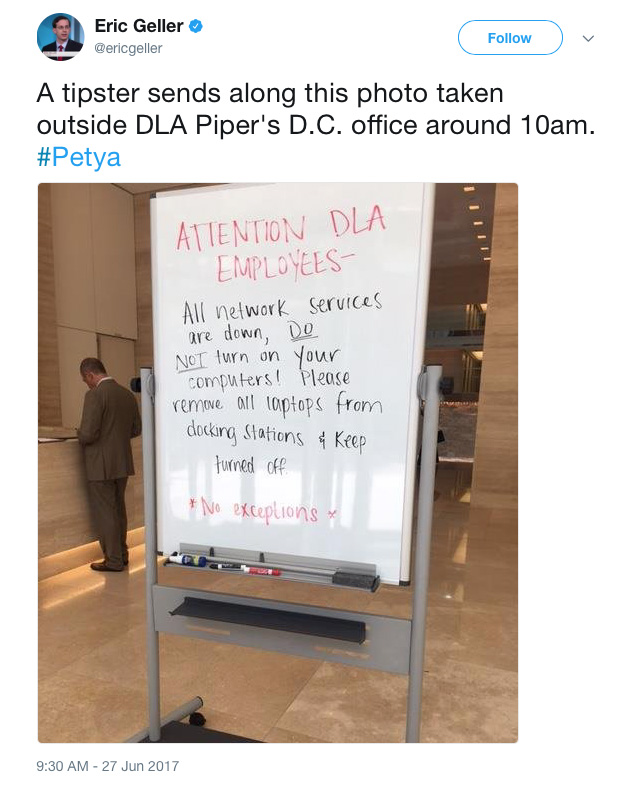
The Day A Mysterious Cyber Attack Crippled Ukraine Bbc Future

Ccas Ethical Hacking Institute In Jaipur Ethical Hacking

Cyber Security Banner Grabbing Tools For Web Application Pen Testing

Cyber Crime Essay Helpful Guide For Everyone
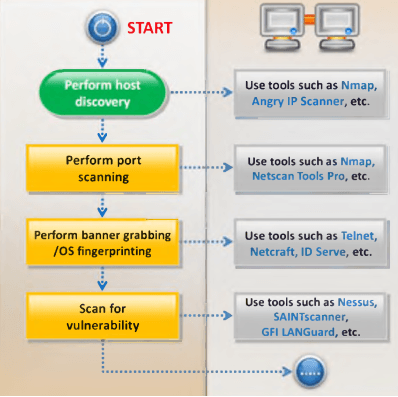
Network Penetration Testing Checklist The Security Blogger

Certified Ethical Hacker Master Ceh Master Ec Council

Modern Cyber Security Threats List Template Infographic

Top 10 High Paying Certifications To Target In 2020 Cyber

Cyber Security With Linux And Networking Ict Academy At Iitk

Firwl Cyber Security Wordpress Theme By Qantumthemes Themeforest

Elite Cyber Security Training Cybernetiv Digital

Top Security Concerns For The Financial Services Industry In 2020

5 Ways To Banner Grabbing

Banner Grabbing With Netcat Sciencedirect

Banner Grabbing With Netcat Sciencedirect

Hacksinfo Digital Helping You Succeed Through Diital Technologies

Cybersecurity Training In Noida Cybersecurity Training Company

Internet Organised Crime Threat Assessment 2018 Europol
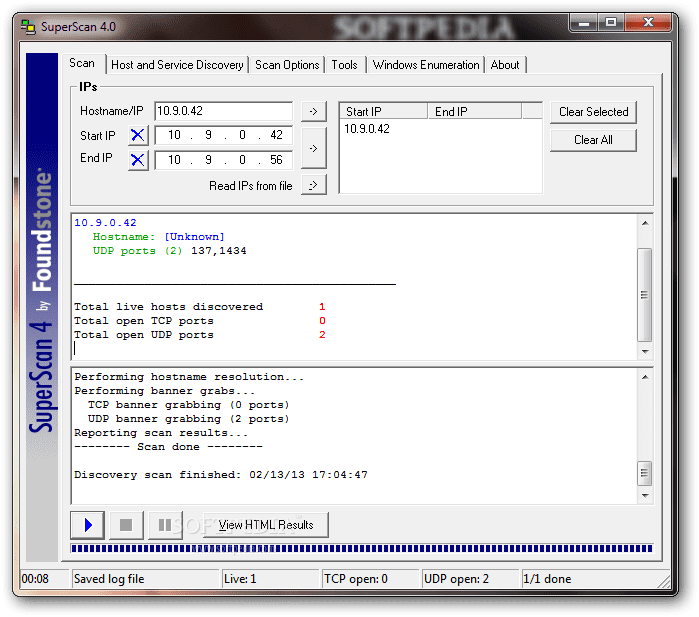
20 Best Hacking Tools In 2020 For Windows Linux And Mac Os X

How To Create A Simple Python Script To Perform Banner Grabbing

Certified Penetration Testing Engineer Pdf Free Download
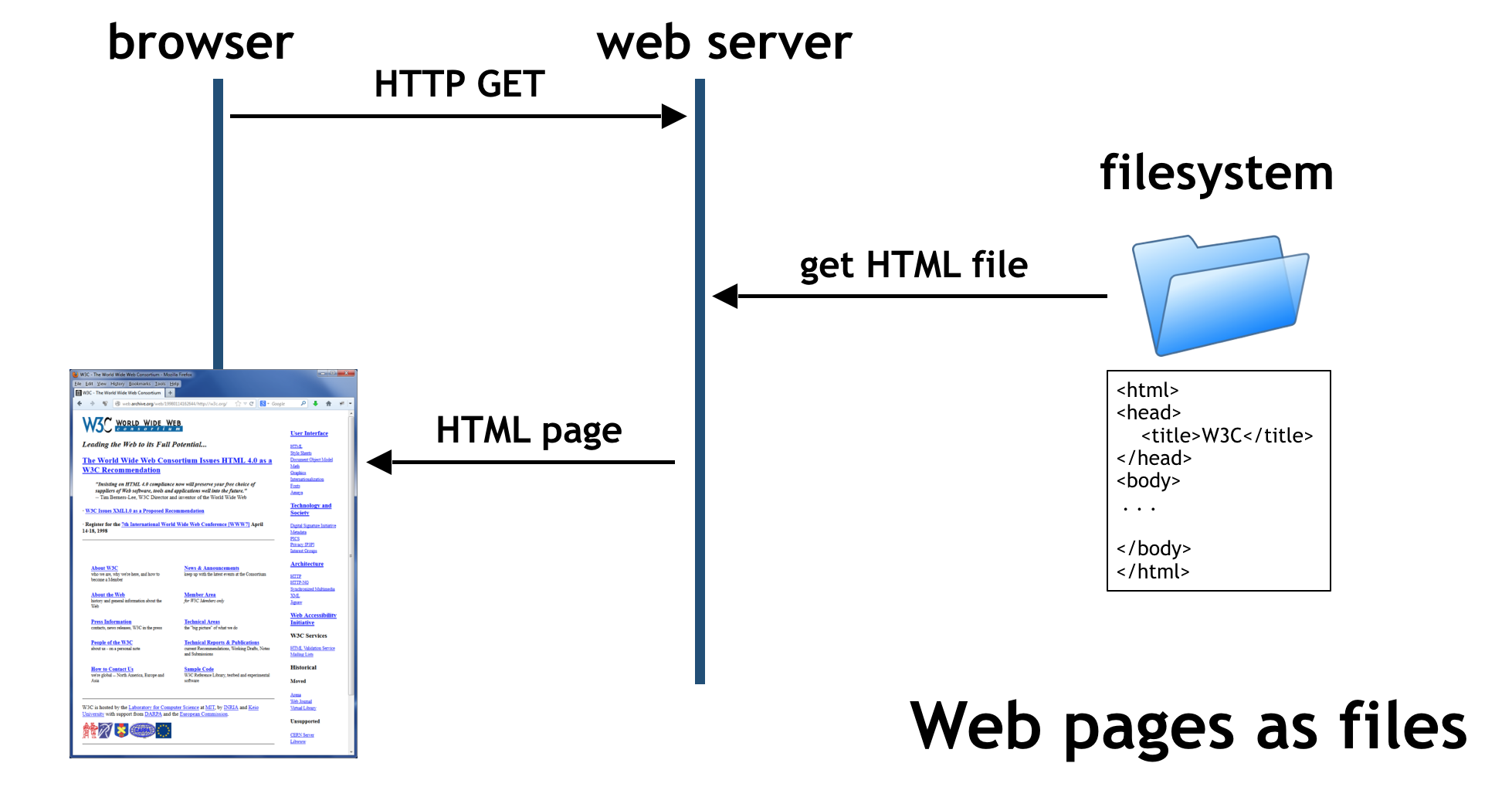
Hacking And Your Cybersecurity Future

What Is A Banner Grabbing Attack 3 Ways To Protect Yourself

What Shodan Is And How To Use It Most Effectively
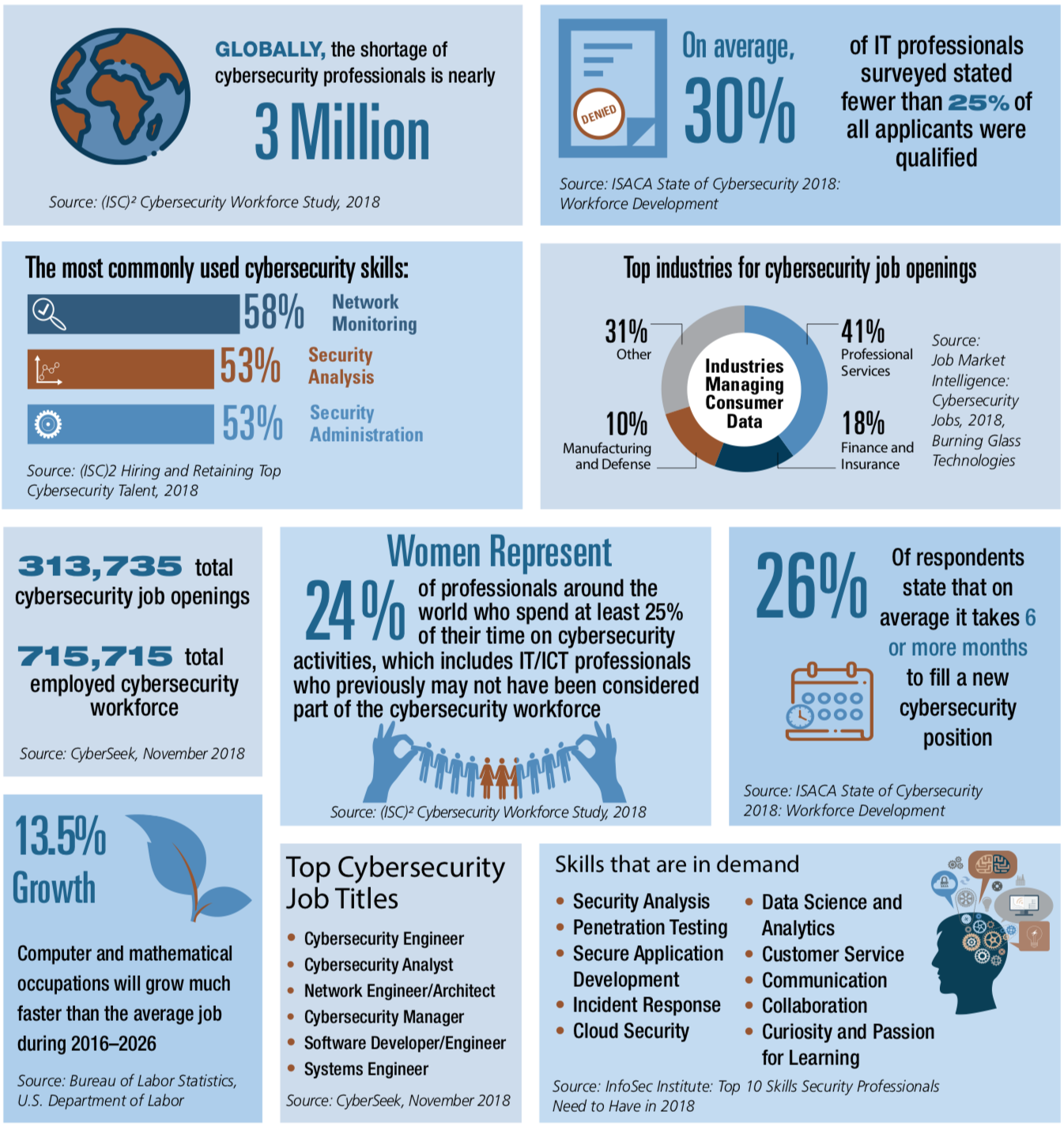
Hacking And Your Cybersecurity Future

Here S How Ethical Hacking Is A Must For Cyber Security

Cyber Security Ethical Hacking Rooman Technologies

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing
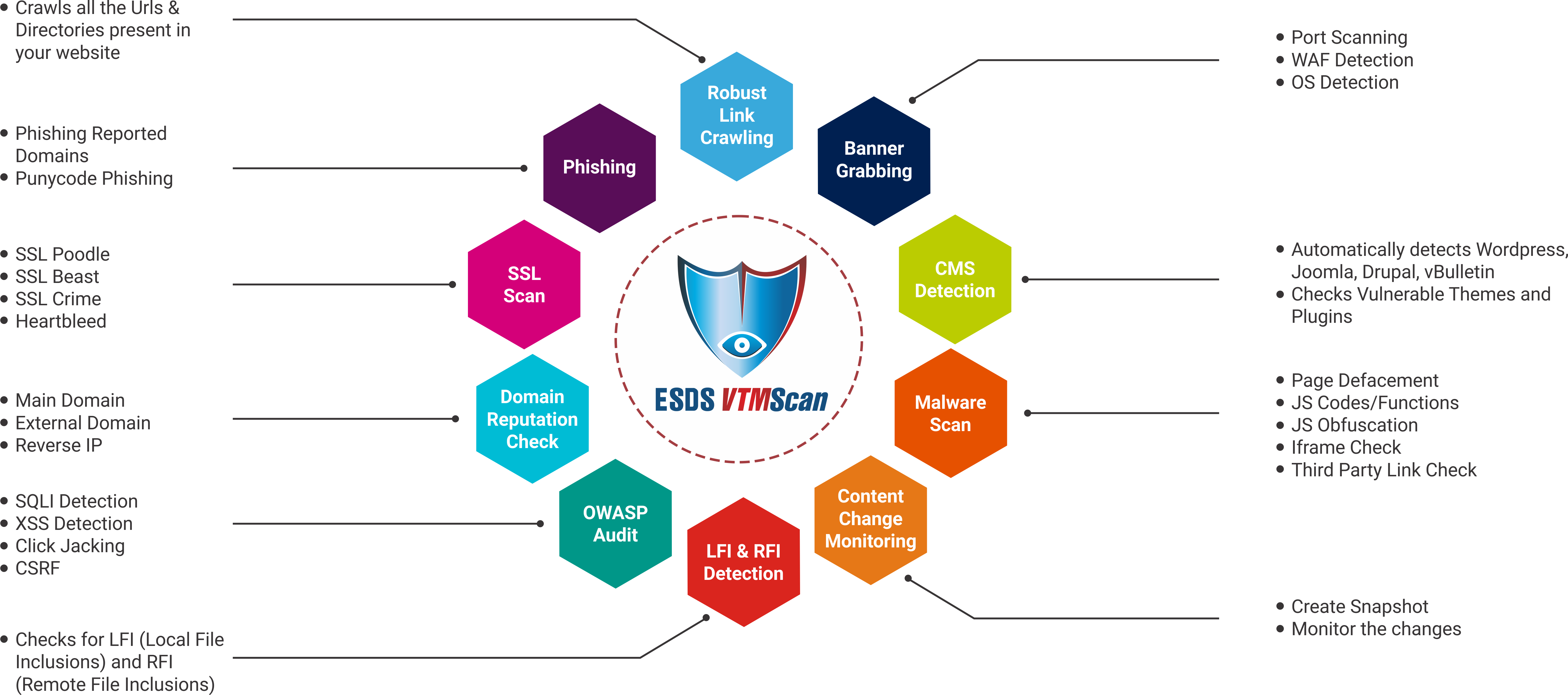
Audit Your Web Security With Esds Vtmscan Vulnerability Scanner

It4yu Banner It4yus

Netcat 101 Security Tutorials

Tower Hamlets College Cyber Security Professional Certification

Ethical Hacking And Cyber Security

Talking Cybersecurity Saas And Early Stage Valuations With
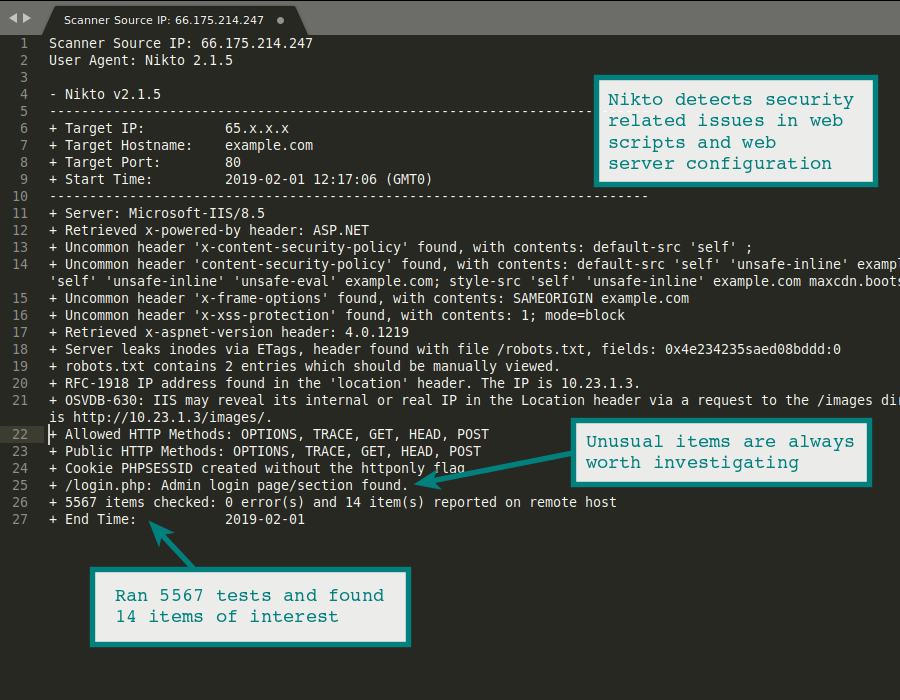
Nikto Web Vulnerability Scanner Hackertarget Com

Netcat Tcp Ip Swiss Army Knife

Ccfis On Twitter Cyberwhisper Cybersecurity Bannergrabbing

How To Use Banner Grabbing To Aid In Reconnaissance Null Byte
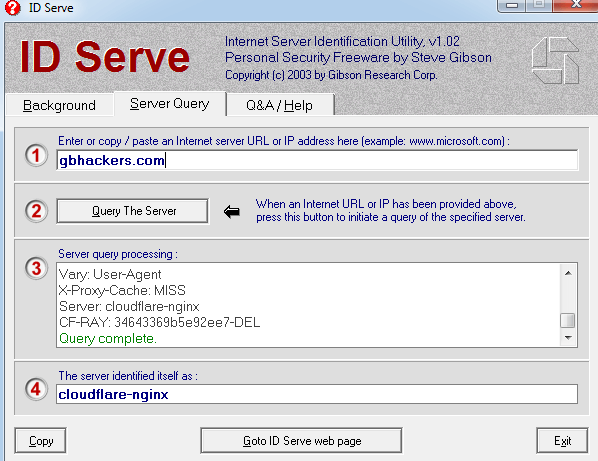
Network Penetration Testing Checklist The Security Blogger

What Is Banner Grabbing Best Tools And Techniques Explained

5 Best Security Practices For Tomcat Servers

Information Disclosure Attacks In Web Applications Netsparker

5 Ways To Banner Grabbing
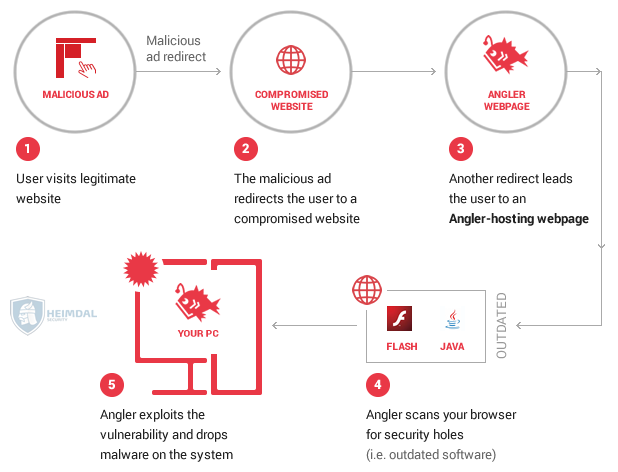
131 Cyber Security Tips That Anyone Can Apply

Hacking Metasploitable Scanning And Banner Grabbing

Eliminate Banner Grabbing In Apache Tomcat

Grab Logo

Mile2 Certified Penetration Testing Engineer Mile2 Cyber

Cyber Security Banner Grabbing Tools For Web Application Pen Testing

40 Cyber Security Mcq With Answers And Explanations Yeah Hub

Web Security Cyber Activity Docsity

Hacking Metasploitable Scanning And Banner Grabbing

5 Best Security Practices For Tomcat Servers

Hacking Cyber Security

Cyber Security Training For Employees The What Why And How

The A To Z Cyber Security It Certification Training Bundle

Rmar Certified Cyber Security Expert Rccse Information Age

Firewall Penetration Testing Steps Methods Tools Purplesec

Powershell Port Scanner And Banner Grabber
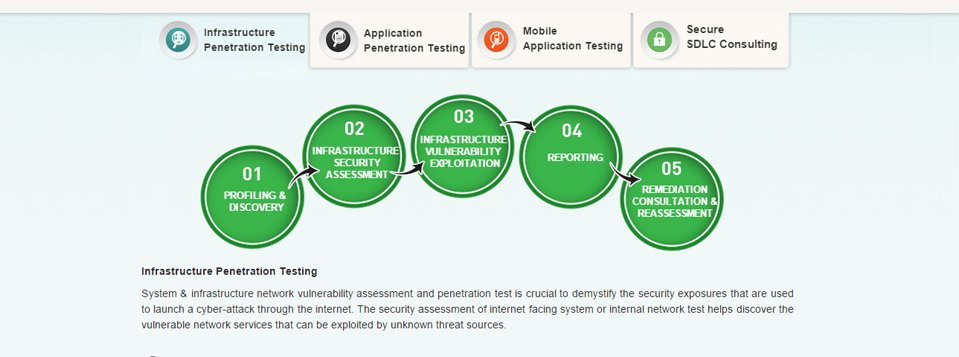
It Security Assurance Services Happiest Minds
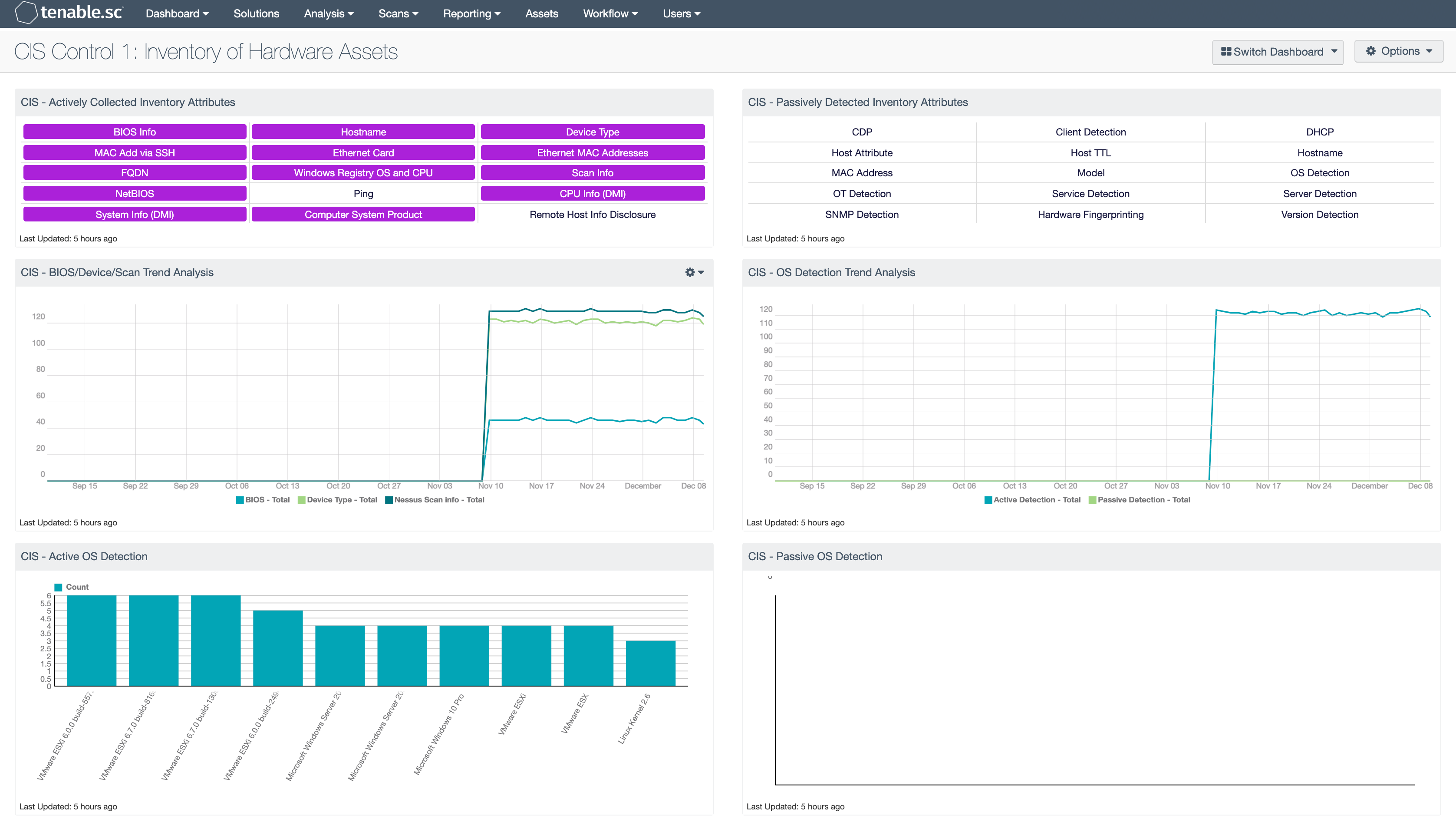
Cis Control 1 Inventory Of Hardware Assets Sc Dashboard Tenable

Resolve To Fix Your Online Security Mess In 2020 Here S How

Which Is The Best Cyber Security Institute In Hyderabad Quora

Develop A Serious Cybersecurity Strategic Plan That Incorporates
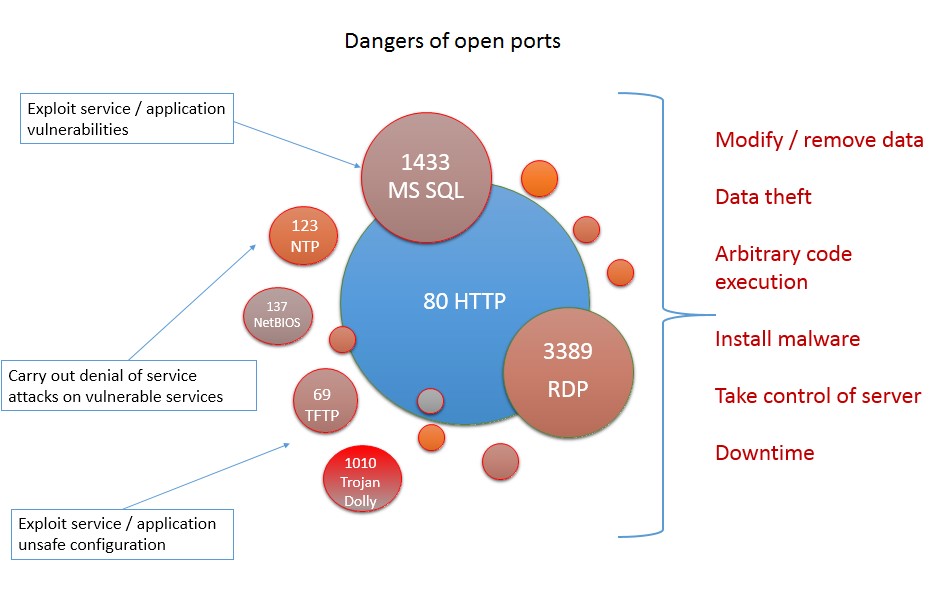
Danger Open Ports Trojan Is As Trojan Does Acunetix

Mask Your Banner To Confuse Hackers Cyber Security Become A

