Le banner grabbing ou le fait de recuperer la banniere dans la langue de moliere est tout simplement le fait de recuperer apres une premiere connexion a un port et un service vise le nom du service qui tourne sur ce port ainsi queventuellement sa version.

Banner grabbing mitigation.
Administrators can use this to take inventory of the systems and services on their network.
Uno de los aspectos a la hora de realizar controles sobre una aplicacion web es la informacion que puede obtenerse a traves de lo que se conoce como banner grabbing.
Hacktivism and black hat hacking.
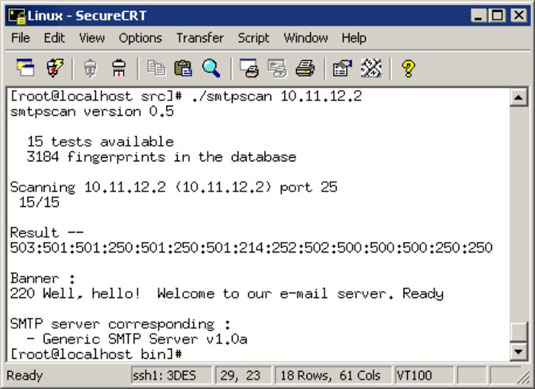
Tools commonly used to perform banner grabbing are telnet which is included with most operating systems and netcat.
Lets explore the different types of banner grabbing techniques.
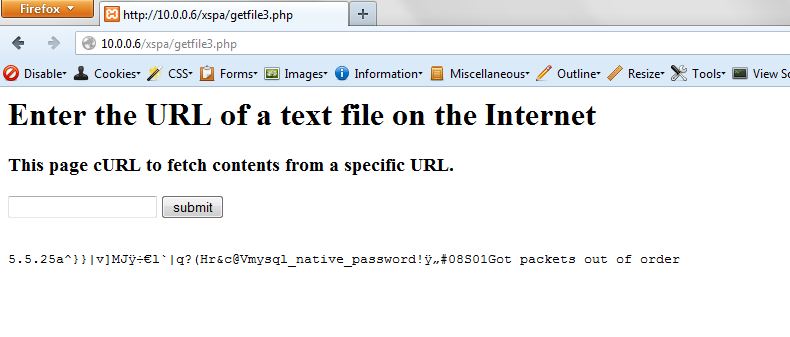
Banner grabbing is a process to collect details regarding any remote pc on a network and the services running on its open ports.
Ports 80 21 and 25 respectively.
If you can customize your banners check with your lawyer about adding a warning banner.
Banner grabbing is often used for white hat hacking endeavors like vulnerability analysis and penetration testing as well as gray hat activities see.
En effet par souci de clarte et.
During an audit i came across banner grabbing findingsand would like to know how to mitigate that on iis and apache server.
Some examples of service ports used for banner grabbing are those used by hyper text transfer protocol http file transfer protocol ftp and simple mail transfer protocol smtp.
This is the most popular type of banner grabbing basically the act of sending packets to the remote host and waiting for their response to analyze the data.
Le banner grabbing.
Banner grabbing is a technique used to gain information about a computer system on a network and the services running on its open ports.
Banner grabbing how to november 22 2016 dave zwickl leave a comment banner grabbing is a footprinting technique used to gather information about the services version running on a systems open ports banner grabbing nd.
Banner screens can be accessed through telnet at the command prompt on the target systems ip address.
A warning banner may also help reduce your business liability in the event of a security breach.

Iis Server Hardening Banner Grabbing Prevention Techniques
Immunit Vulnerability Disclosure Cisco Meeting Server Cms

Elevation Of Privilege

Iis Server Hardening Banner Grabbing Prevention Techniques

Chapter 13 Vulnerability Assessment And Data Security
Iis Server Hardening Banner Grabbing Prevention Techniques

Information Disclosure Attacks In Web Applications Netsparker

Hoboken Train Crash Might Have Been Mitigated By Modern Bumpers
Comptia Security Attack Types And Mitigation Courses
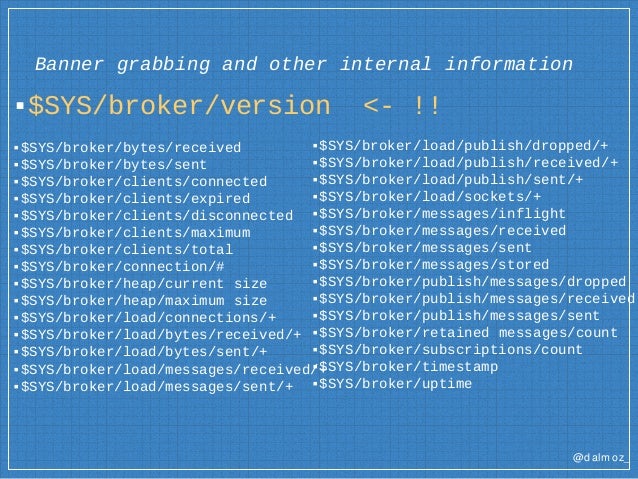
Mqtt Iot Explore Exploit Bsidestlv 2017 June 2017

How Web Servers Work Web Servers Use Hyper Text Transfer Protocol
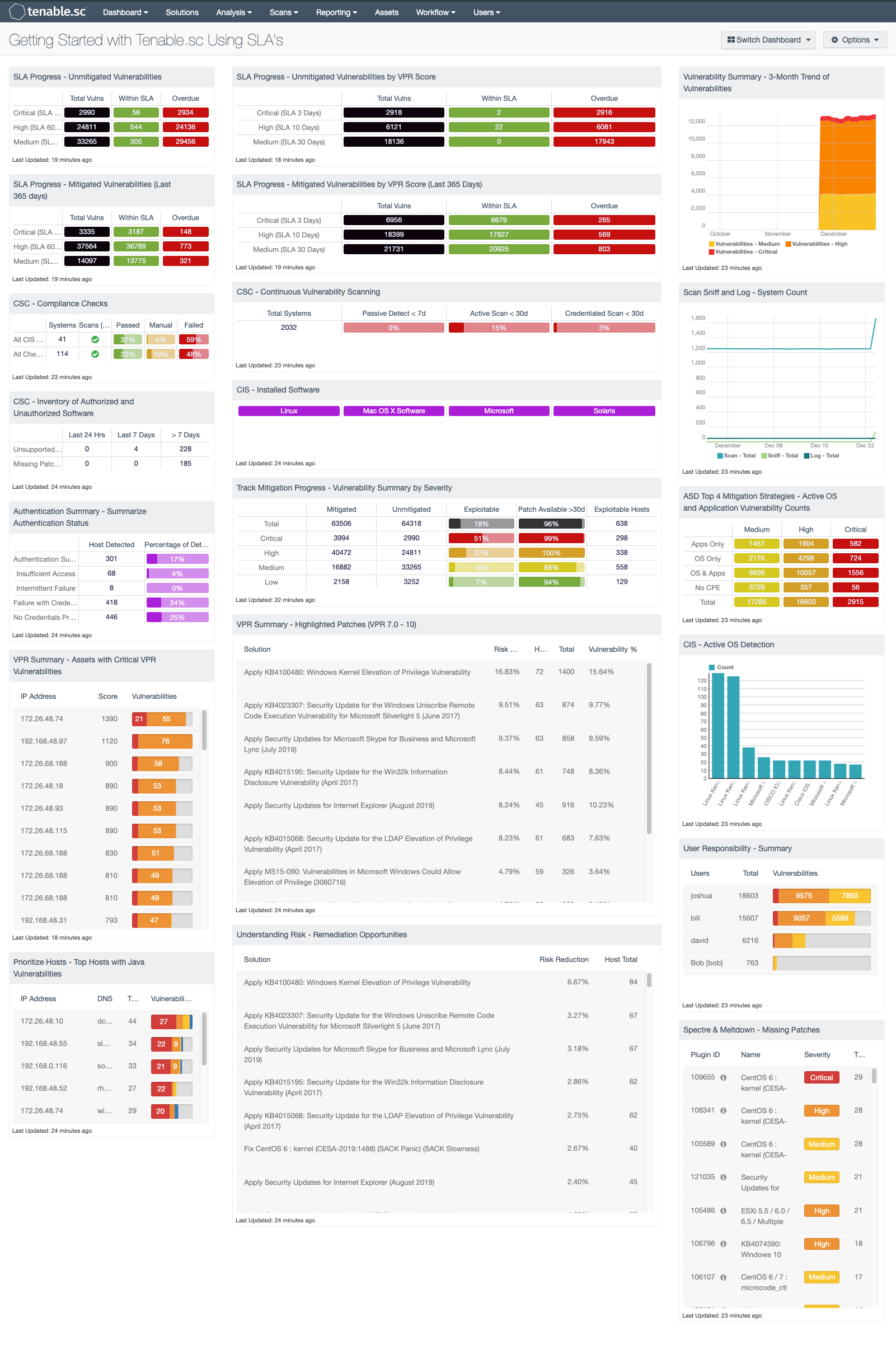
Getting Started With Tenable Sc Using Sla S Sc Dashboard Tenable

Inferring And Mitigating Internet Scale Unsolicited Iot Devices A

Fxswmppkm0ypgm

The False Promises Of Hydropower How Dams Fail To Deliver The

Simulated Os Detection By Banner Grabber Time Versus Syscalls

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Iis Server Hardening Banner Grabbing Prevention Techniques

Information Disclosure Attacks In Web Applications Netsparker

Iis Server Hardening Banner Grabbing Prevention Techniques
Non Root Containers Kubernetes Cve 2019 11245 And Why You Should Care
W4rri0r Hacking Is Not A Crime It S An Art Of Awareness

Banner Blindness Wikipedia

Ec Council Certified Ethical Hacker Version 6 Pdf Free Download

Good Food Good Farming Campaign Is Cooking Up A Storm Arc2020

Banner Grabbing With Netcat Sciencedirect

Security Guide To Network Security Fundamentals Fifth Edition

Web Application Threats And Vulnerabilities Web Server Hacking And

Mqtt Iot Explore Exploit Bsidestlv 2017 June 2017

Chapter 13 Vulnerability Assessment And Data Security

Evaluation Of The Ability Of The Shodan Search Engine To Identify
Offensive Netcat Ncat From Port Scanning To Bind Shell Ip

Eliminate Banner Grabbing In Apache Tomcat

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

A Very Incomplete Diagram Of Network Attacks Pdf Free Download

Purplesec Cyber Security Services Purple Sec On Pinterest

Hacking Articles Raj Chandel S Blog

Cs3695 M6 109 Network Vulnerability Assessment Risk Mitigation

Vulnerability Testing Of Windows 10

Web Application Security Services Ppt By Velevate11 Issuu

Some Election Officials Scrambling To Address Coronavirus Concerns

Smb Version Detection In Masscan Security Boulevard

Dhs Em Earthquake Mitigation
Land Free Full Text Coupled Relationship Between Rural

Canonicalization Attack Updated 2019

Intersec 2020 Hanwha Techwin Showcases Ai Technology Security

Netcat Vs Ncat The Big Confusion Cybrary

Information Disclosure Attacks In Web Applications Netsparker

Penetration Testing Security The Offensive Way

Eliminate Banner Grabbing In Apache Tomcat

Confidential Information Information Disclosure

Simulated Os Detection By Banner Grabber Time Versus Syscalls

What Is Banner Grabbing Best Tools And Techniques Explained

Xu Magazine Issue 18 By Xu Magazine Issuu

Ceh Ethical Hacking And Countermeasures It Training

How Conservative American Money Helped The Religious Right Take

Black Hat Hackers Paradise Posts Facebook

In The Midst Of The Current Storm We Need Perspective And

Chapter 13 Vulnerability Assessment And Data Security

Banner Grabbing With Netcat Sciencedirect

Banner Grabbing With Netcat Sciencedirect

Banner Grabbing With Netcat Sciencedirect

A Step By Step Guide To Vulnerability Assessment

On The Campaign Trail 2020 New Hampshire Edition Tablet Magazine

Information Vulnerability Disclosure
Nessus Scan Meraki

Penetration Testing Security The Offensive Way

Comptia Security Tutorial Deterrent And Mitigation Techniques

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

A Very Incomplete Diagram Of Network Attacks Pdf Free Download

Urgent 11 New Ics Threat Signatures By Nozomi Networks Labs

Denial Of Service

Simulated Os Detection By Banner Grabber Time Versus Syscalls

Information Disclosure Attacks In Web Applications Netsparker

Hacking Web Server Defiana Arnaldy M Si Ppt Download
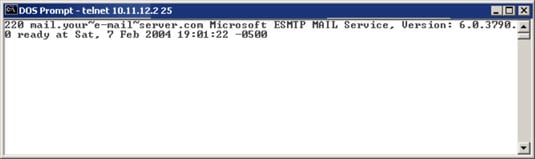
How Hackers Grab Banners To Penetrate Your Network Dummies

A Very Incomplete Diagram Of Network Attacks Pdf Free Download

Iis Server Hardening Banner Grabbing Prevention Techniques

Chapter 15 Presentation

Security Guide To Network Security Fundamentals Fifth Edition

Information Disclosure Attacks In Web Applications Netsparker

Https Www Sans Org Cyber Security Summit Archives File Summit Archive 1510711505 Pdf

Simulated Os Detection By Banner Grabber Time Versus Syscalls

Do Penetration Testing And It Security For Your Company By
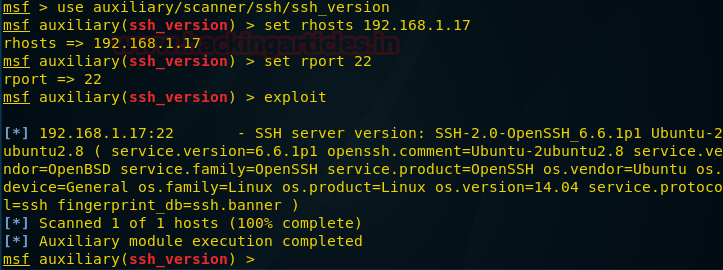
Hacking Articles Raj Chandel S Blog

Chapter 13 Vulnerability Assessment And Data Security

Iis Server Hardening Banner Grabbing Prevention Techniques
Cis Control 1 Inventory Of Hardware Assets Sc Dashboard Tenable

Iis Server Hardening Banner Grabbing Prevention Techniques

Information Disclosure Attacks In Web Applications Netsparker

How Attackers Exploit Information For Their Own Purposes

Finding Cve 2018 10933 Affected Hosts With Masscan Juho Mikkonen

Solutionbase Audit Windows Host Security With The Free Superscan

Banner Grabbing With Netcat Sciencedirect

Banner Grabbing With Netcat Sciencedirect

Banner Grabbing With Netcat Sciencedirect
Mqtt Iot Explore Exploit Bsidestlv 2017 June 2017

Banner Grabbing With Netcat Sciencedirect