
5 Ways To Banner Grabbing

Information Disclosure Attacks In Web Applications Netsparker

Striker Offensive Vulnerability Scanner Sectechno

Configuring Your Web Server To Not Disclose Its Identity Acunetix

Red Hawk V2 All In One Tool For Information Gathering And

Cyber Security Banner Grabbing Tools For Web Application Pen Testing

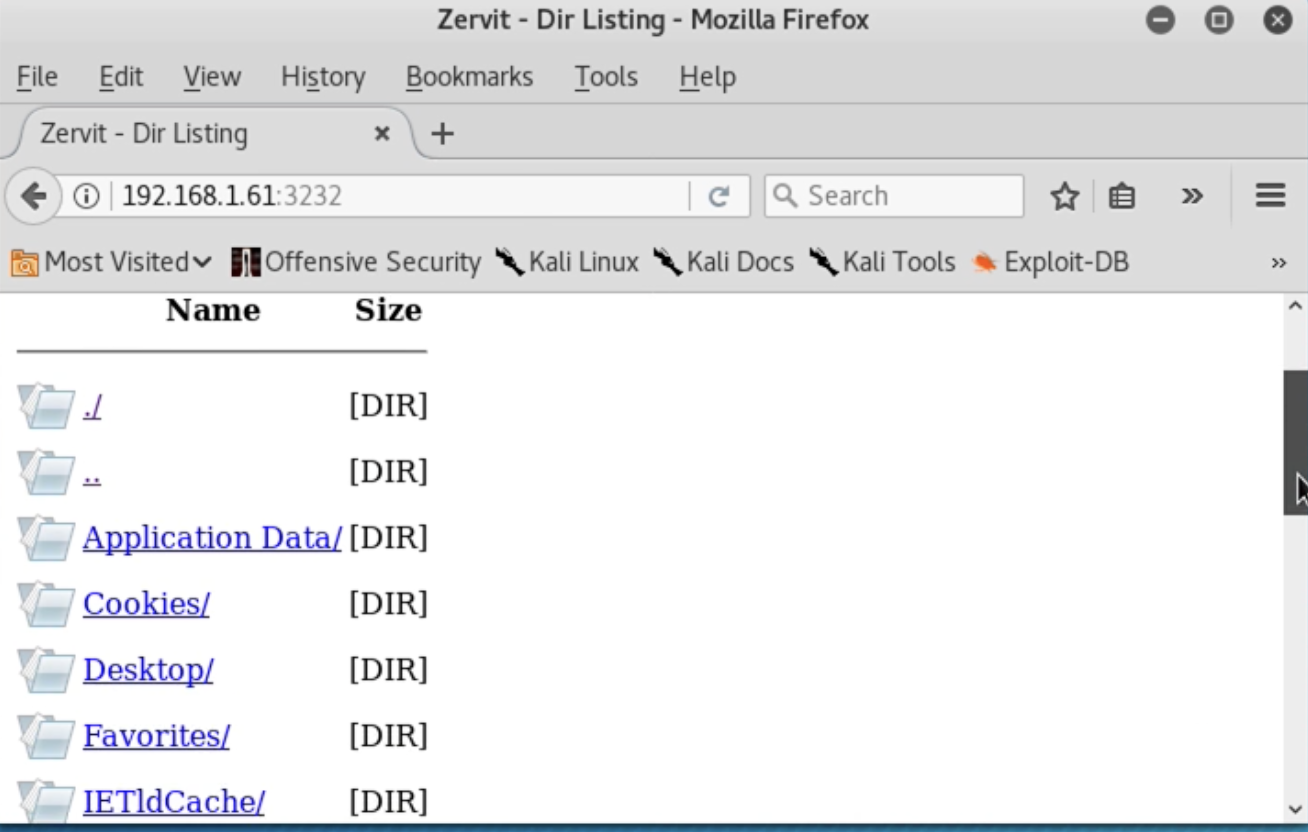
Banner Grab Food

Evaluation Of Network Port Scanning Tools Pdf Free Download
Using Nmap Scripts Nmap Banner Grab Linux Hint
Solved If Someone Could Please Help Me And Explin This St
Banner Grabbing To Dos And Memory Corruption Infosec Write Ups

Banner Grabbing With Telnet Cybrary
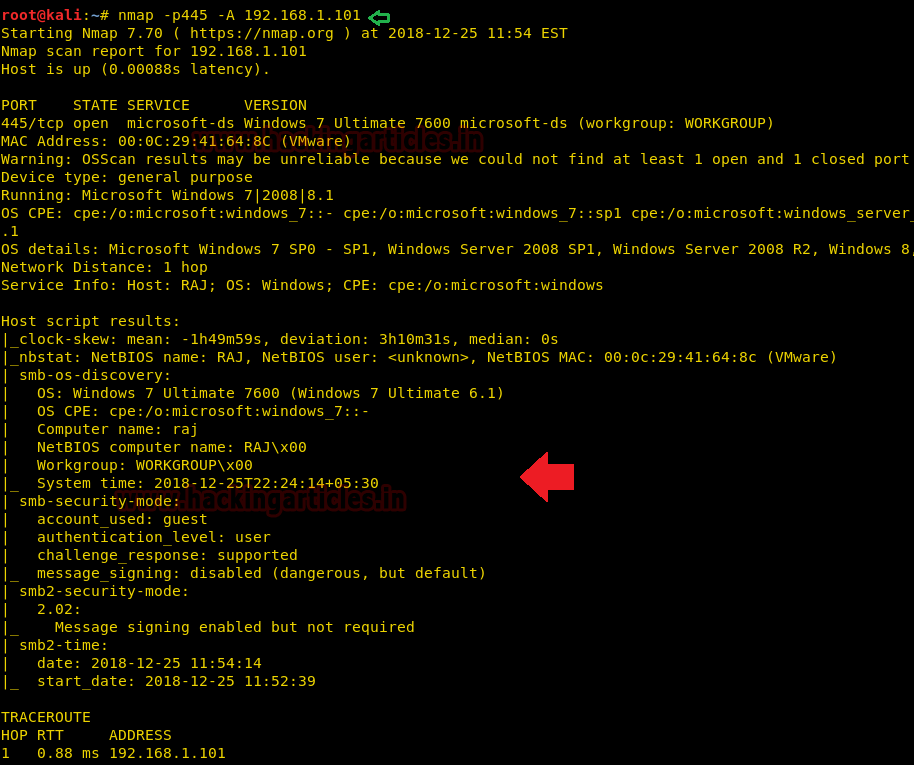
Smb Penetration Testing Port 445
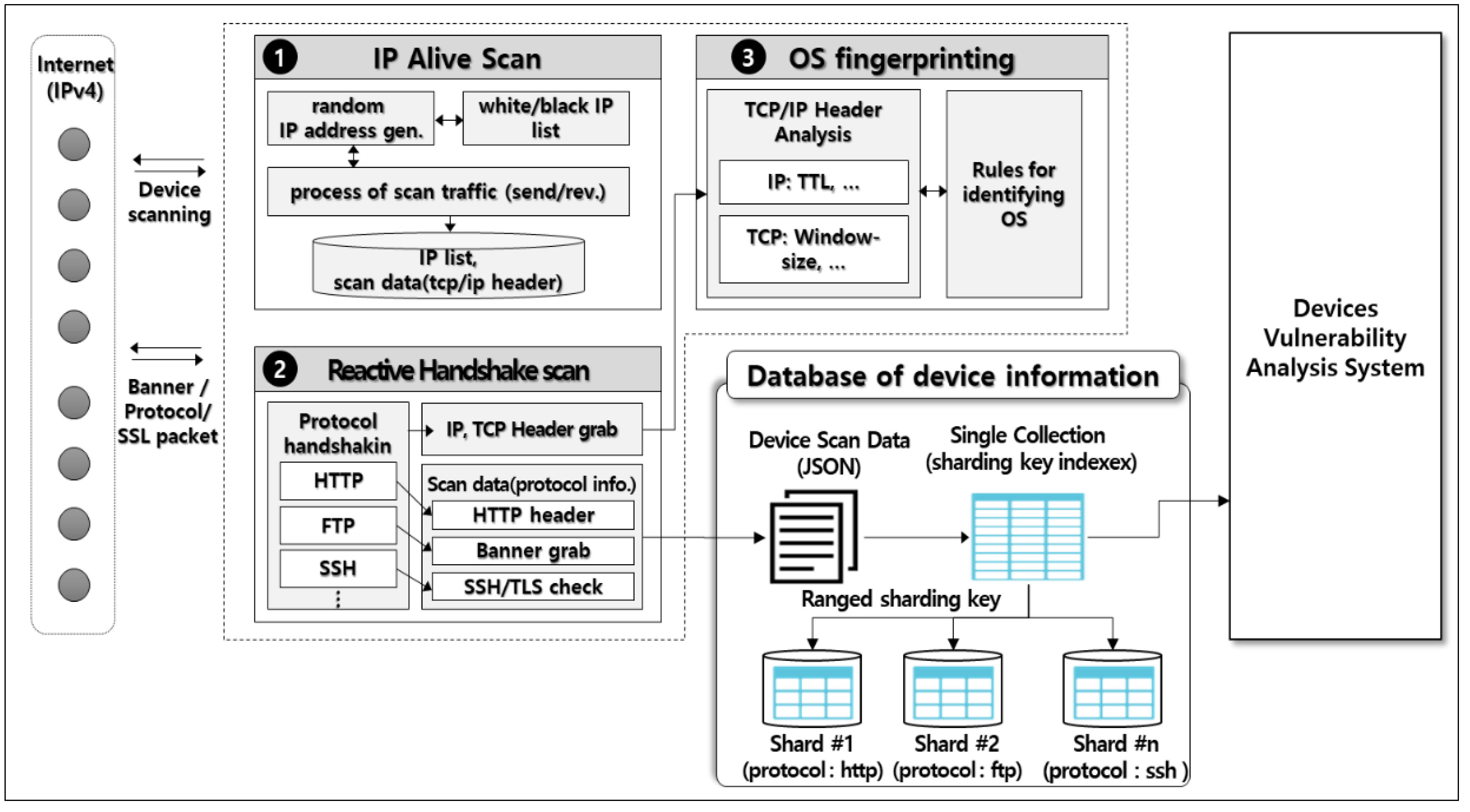
Symmetry Free Full Text An Intelligent Improvement Of Internet

Confidential Information Information Disclosure
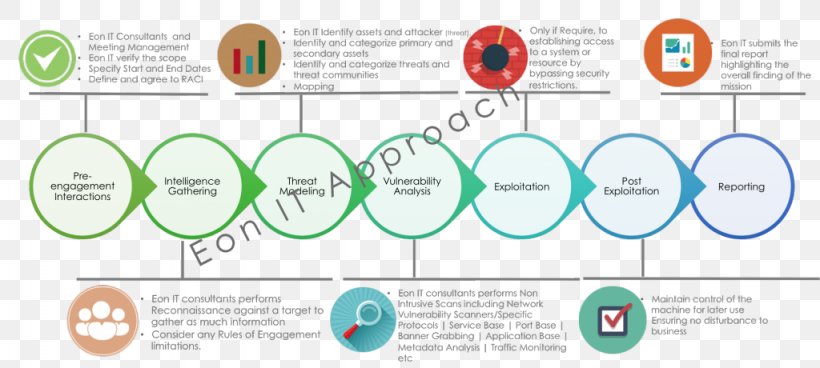
Penetration Test Information Security Information Technology

Https Www Mdpi Com 2073 8994 10 5 151 Pdf

5 Ways To Banner Grabbing

Simulated Os Detection By Banner Grabber Time Versus Syscalls

Information Disclosure Attacks In Web Applications Netsparker

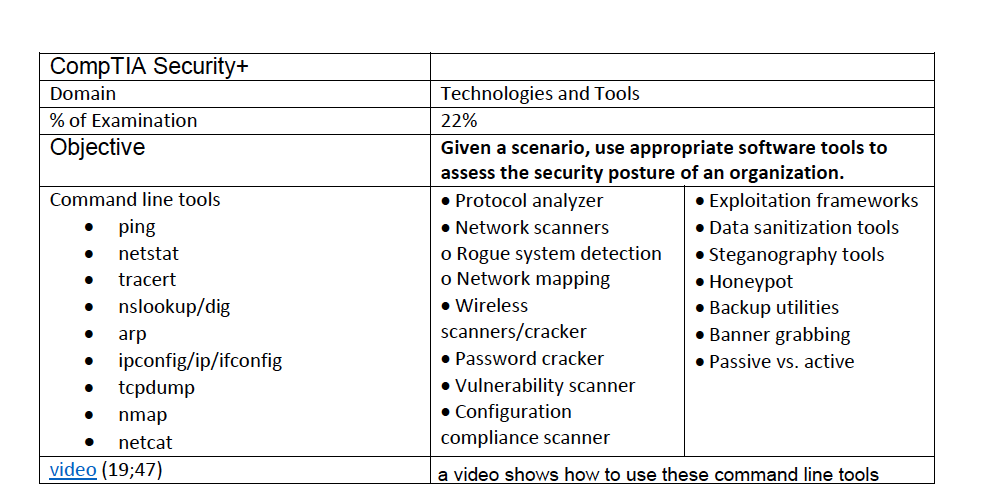
Pace It Security 3 7 Overview Of Security Assessment Tools

What Is Banner Grabbing Best Tools And Techniques Explained

Information Legal Disclosure

Maltego Best Vulnerability Scanning Tool Using Kali Linux

What Shodan Is And How To Use It Most Effectively

Nt0yq3o6kxfnnm

Cyber Security Banner Grabbing Tools For Web Application Pen Testing

Netbios Scan Results Download Scientific Diagram

Banner Grabbing With Netcat Sciencedirect
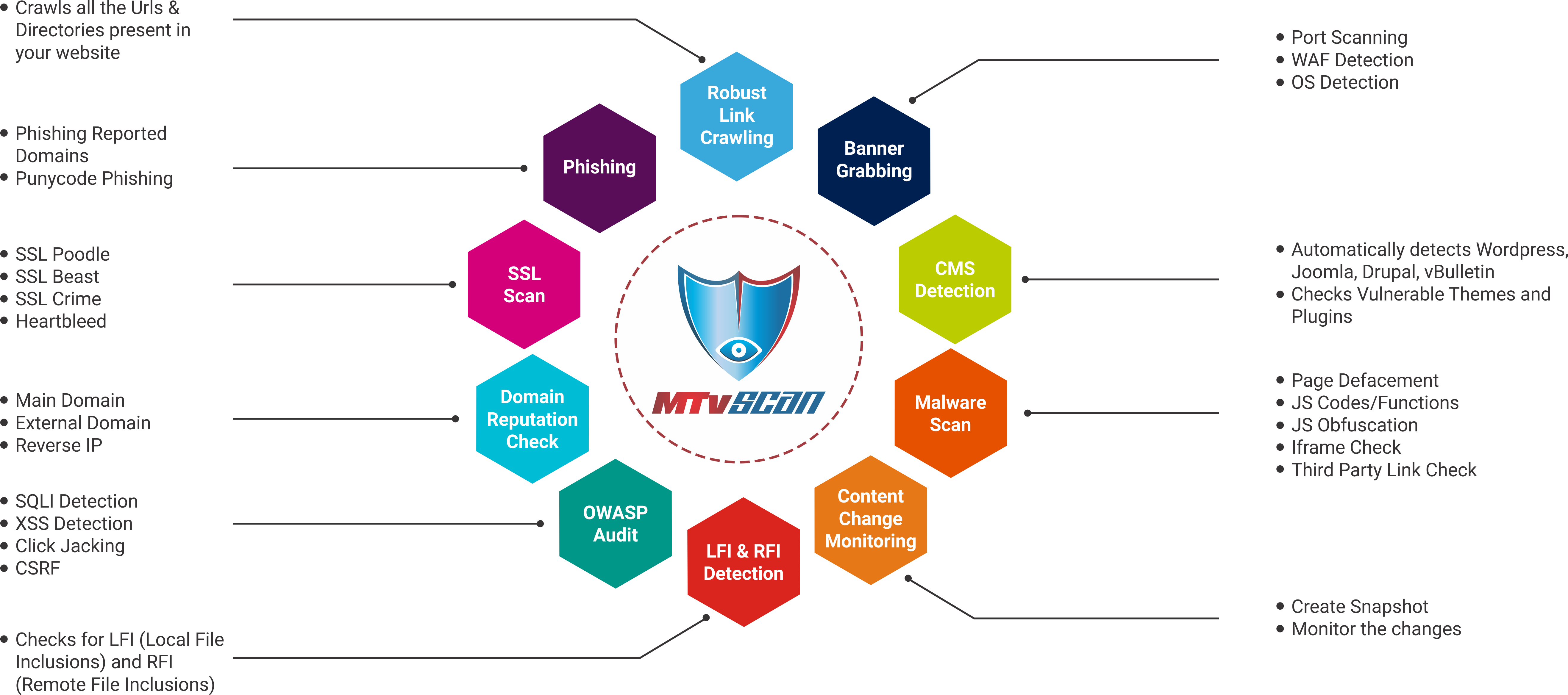
Mtvscan Website Malware Scanning Features Manoj Nagesh Medium

Dotdotpwn The Directory Traversal Fuzzer Cyberpunk

Agenda 9 30 10 45 Assessing Network Security 10 45 11 00 Break

Cloudflare Open Sources Network Vulnerability Scanner Techbizweb

Information Disclosure Attacks In Web Applications Netsparker

How To Use Sqlmap Blogs

Eliminate Banner Grabbing In Apache Tomcat

Firewall Penetration Testing Steps Methods Tools Purplesec

Beginner S Guide To Banner Grabbing Project Nirvana 2030

Beginner S Guide To Banner Grabbing Project Nirvana 2030

Smb Penetration Testing Port 445

Banner Grabbing With Netcat Sciencedirect

Banner Grabbing

Banner Grabbing And Port Scanning Using Scanline Penetration Testing

Maltego Best Vulnerability Scanning Tool Using Kali Linux

Hacking Exposed 7 Network Security Secrets Solutions Ppt Video

Security Guide To Network Security Fundamentals Fifth Edition
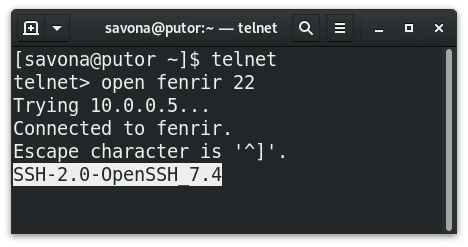
Nt0yq3o6kxfnnm
Tips For An Information Security Analyst Pentester Career Ep 36

Iis Server Hardening Banner Grabbing Prevention Techniques

Analysis Of Field Data On Web Security Vulnerabilities

Web Application Penetration Testing Course Cybersecurity

Cyber Security Banner Grabbing Tools For Web Application Pen Testing

Libssh Scanner Script To Identify Hosts Vulnerable To Cve 2018 10933

Banner Grabbing Search

Tools And Techniques To Discover Security Threats And Vulnerabilities

Eliminate Banner Grabbing In Apache Tomcat

How To Perform A Nmap Vulnerability Scan Using Nse Scripts
Banner Grabbing To Dos And Memory Corruption Infosec Write Ups
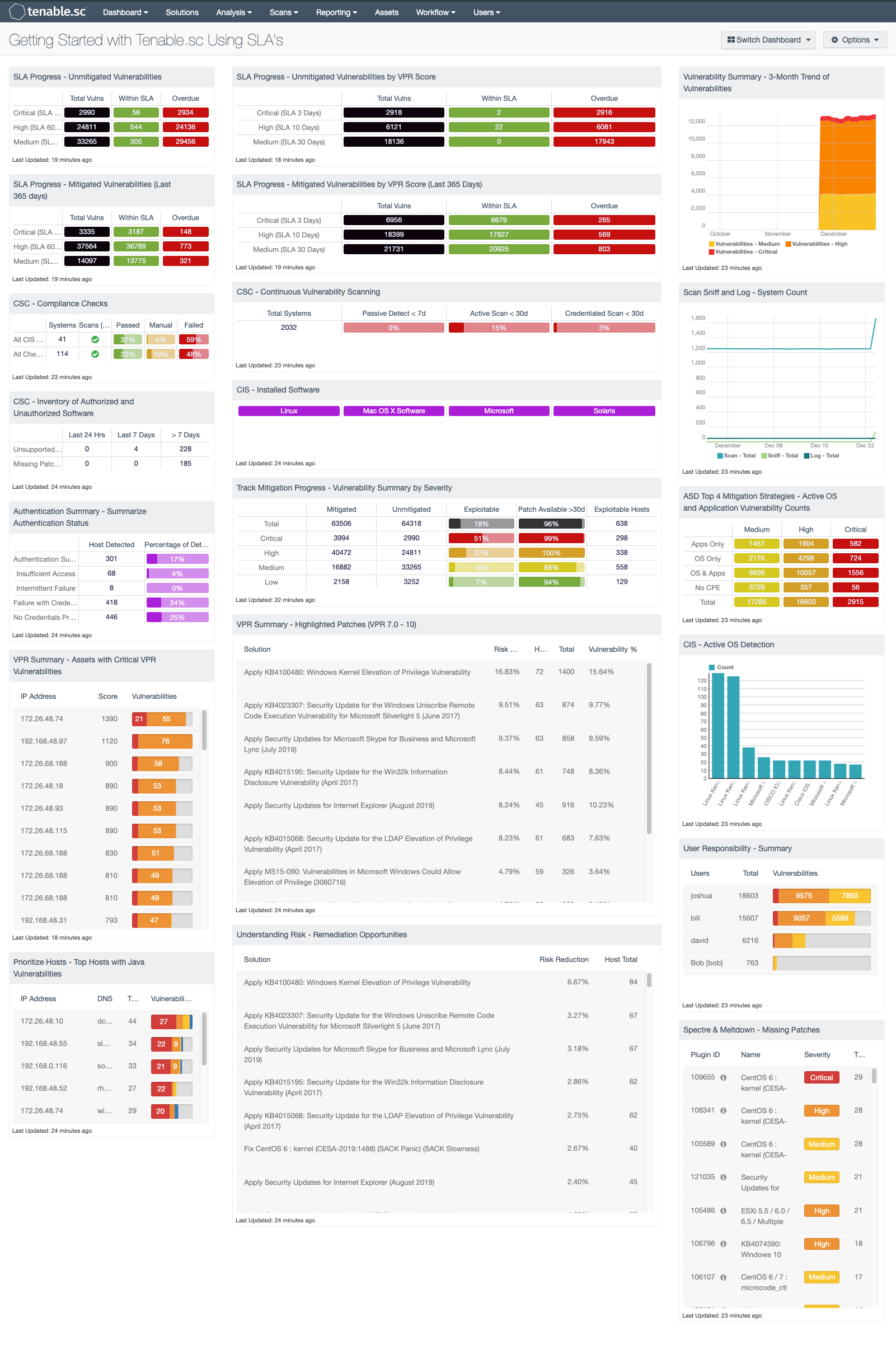
Getting Started With Tenable Sc Using Sla S Sc Dashboard Tenable

5 Ways To Banner Grabbing

Hacking Metasploitable Scanning And Banner Grabbing
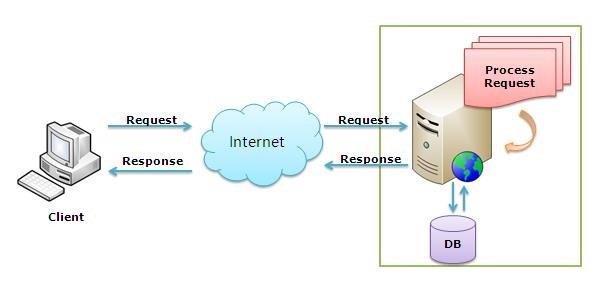
Iis Server Hardening Banner Grabbing Prevention Techniques

Information Disclosure Attacks In Web Applications Netsparker

Cryptex Seguridad De La Informacion Network Penetration Testing
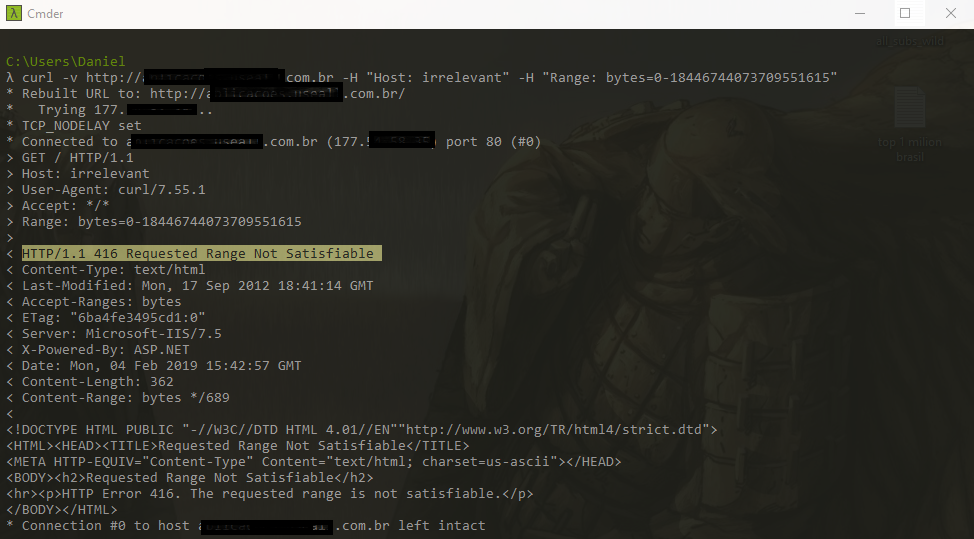
Banner Grabbing To Dos And Memory Corruption Infosec Write Ups
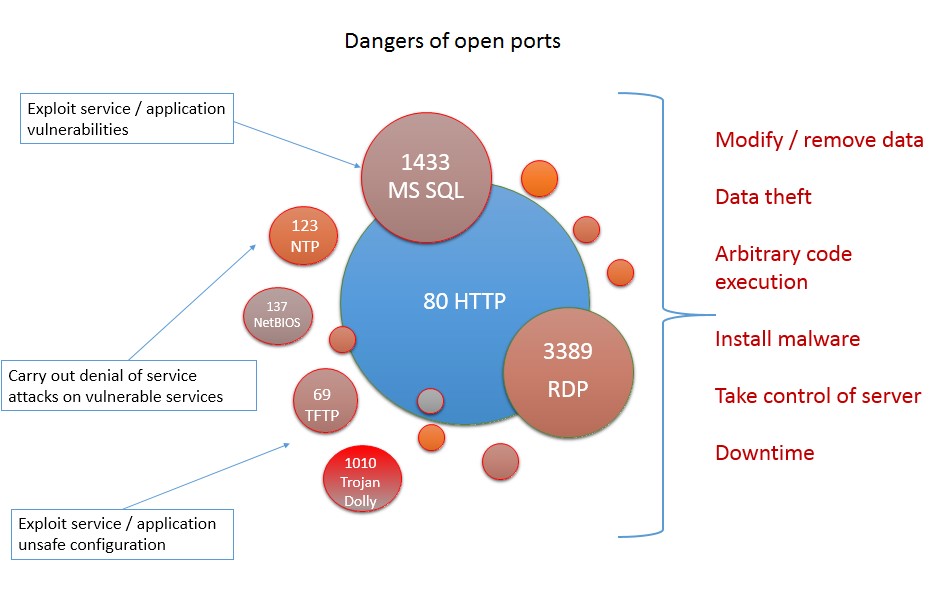
Danger Open Ports Trojan Is As Trojan Does Acunetix

Https Www Sans Org Cyber Security Summit Archives File Summit Archive 1510711505 Pdf
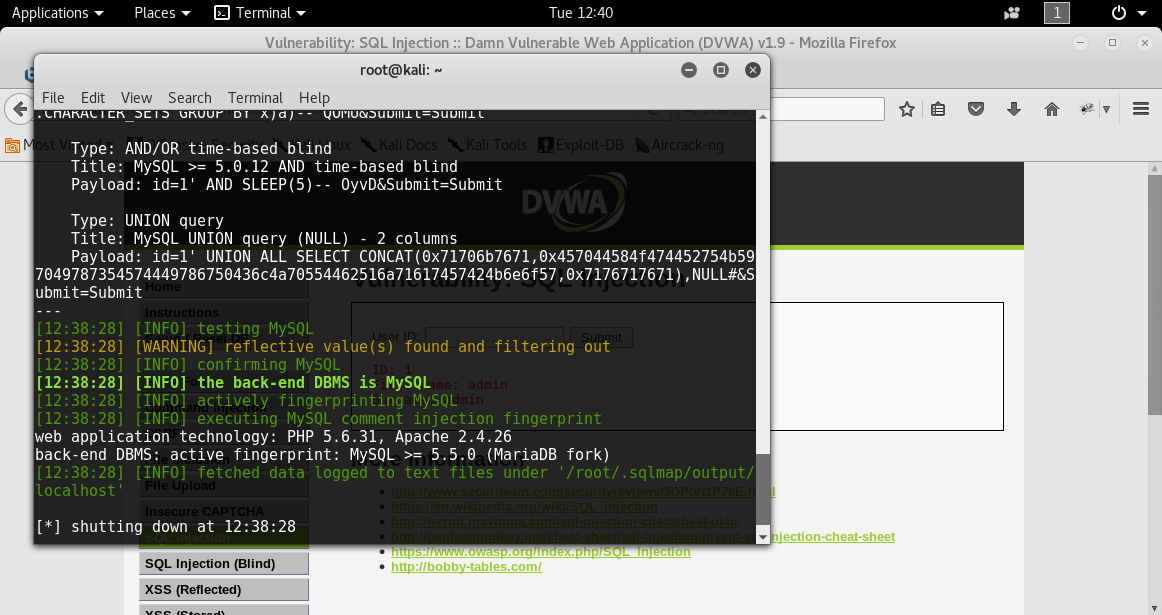
How To Use Sqlmap Blogs
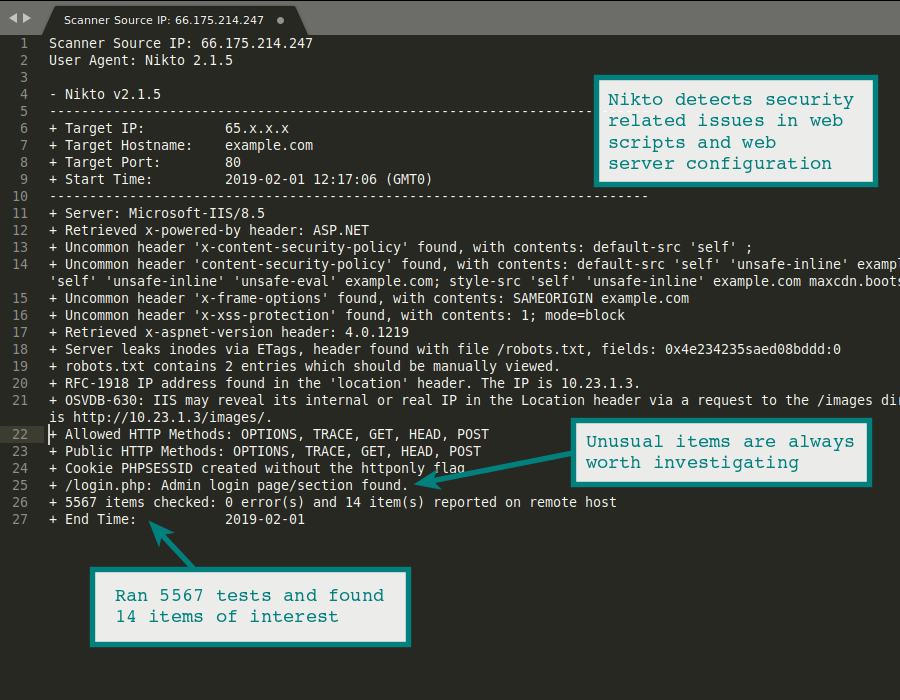
Nikto Web Vulnerability Scanner Hackertarget Com

Http Banner Grabbing Using Telnet Penetration Testing

Web Application Threats And Vulnerabilities Web Server Hacking And
Introducing Flan Scan Cloudflare S Lightweight Network

What Is Banner Grabbing Best Tools And Techniques Explained

Banner Grabbing

Module 04 Simple Banner Grabbing Socket Programming With Python

Information Disclosure Attacks In Web Applications Netsparker

Banner Grabbing With Netcat Sciencedirect

How To Use Offensive Techniques To Enrich Threat Intelligence
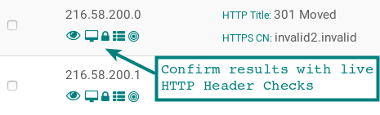
Banner Grabbing Search

A Step By Step Guide To Vulnerability Assessment
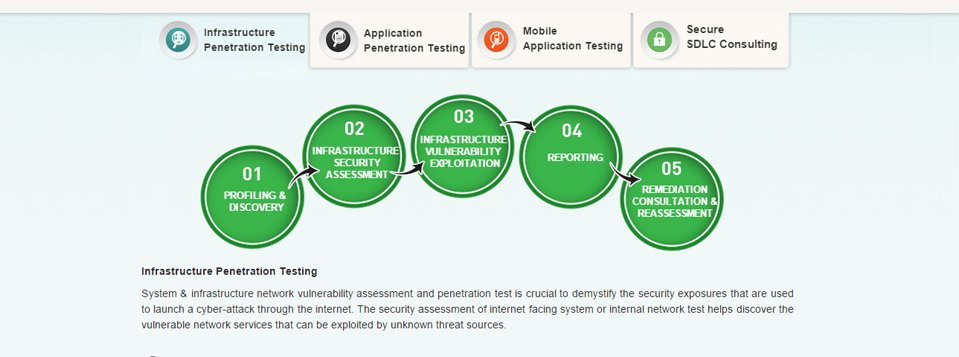
It Security Assurance Services Happiest Minds

Cartoon Disclosure
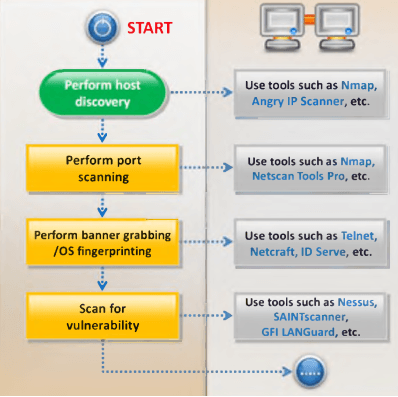
Network Penetration Testing Checklist The Security Blogger
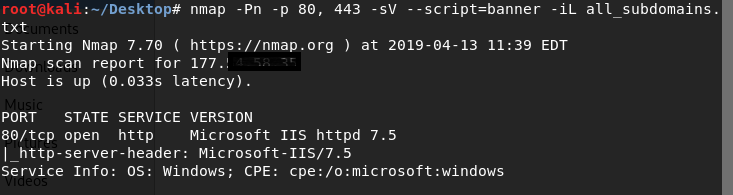
Banner Grabbing To Dos And Memory Corruption Infosec Write Ups

Comptia Security Study Guide Sy0 401 Chapter 9 Malware
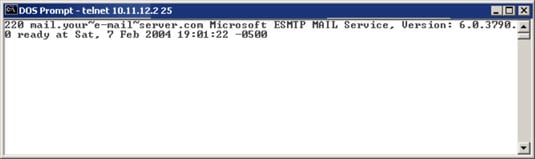
How Hackers Grab Banners To Penetrate Your Network Dummies

Do Penetration Testing And It Security For Your Company By

Banner Grabbing

Eliminate Banner Grabbing In Apache Tomcat

Http Citeseerx Ist Psu Edu Viewdoc Download Doi 10 1 1 682 8622 Rep Rep1 Type Pdf

Banner Grabbing With Netcat Sciencedirect

Report A Security Vulnerability Wpsec Com Online Wordpress
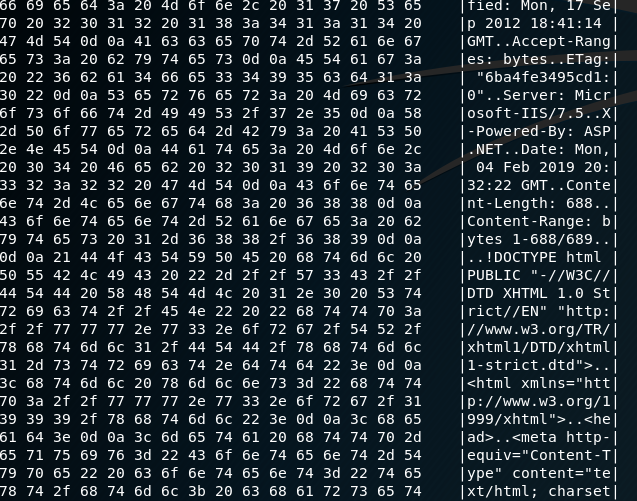
Banner Grabbing To Dos And Memory Corruption Infosec Write Ups

How To Locate Exploit Devices Vulnerable To The Libssh Security

Banner Grabbing With Cmd Demo Youtube

Never Stop At Banner Grabbing I M Gaurav Narwani

Beginner S Guide To Banner Grabbing Project Nirvana 2030

Tips For An Information Security Analyst Pentester Career Ep 36

