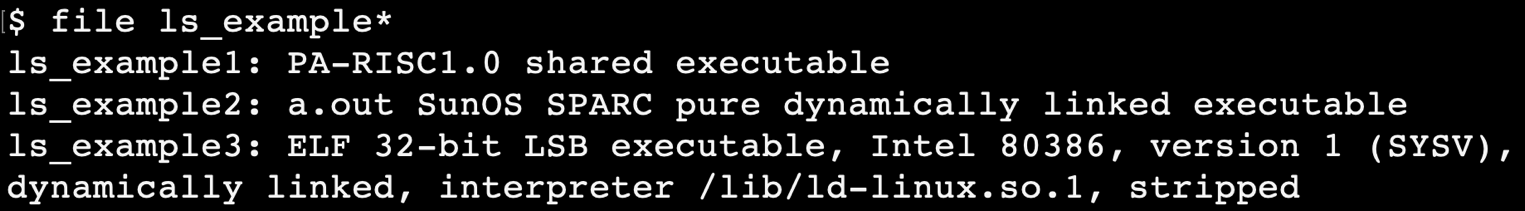
Active banner grabbing techniques involve opening a tcp or similar connection between an origin host and a remote host.
Is banner grabbing active or passive.
In only banner grabbing i could see the passive argument as you arent really doing anything more than a full connection to the port ie.
Administrators can use this to take inventory of the systems and services on their network.
This is the most risky approach to banner grabbing as its often detected by some ids.
There are two types of banner grabbing.
Banners are intended for network administration.
It can be considered active as your connection will be logged in the remote system.
Banners usually contain information about a service such as the version number.
If you were actually crafting protocol aware packets to solicit a response that would certainly be active.
Banner grabbing is a technique used to gain information about a computer system on a network and the services running on its open ports.
In this way passive reconnaissance may differ greatly in cyber warfare activity than in penetration testing.
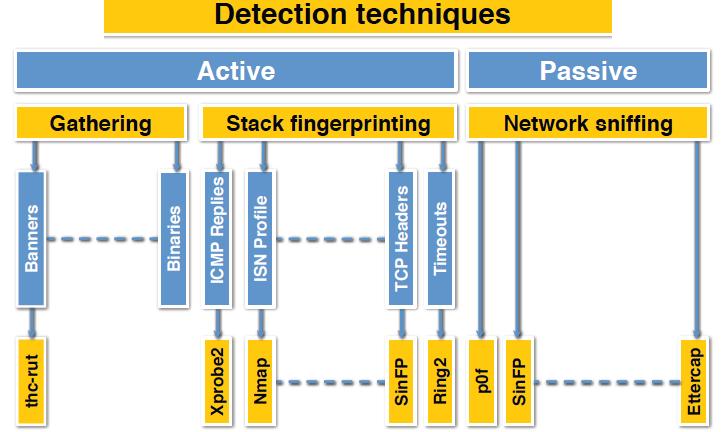
Banner grabbing or os fingerprinting is the method to determine the operating system running on a remote target system.
This banner search is a passive information gathering tool no testing.
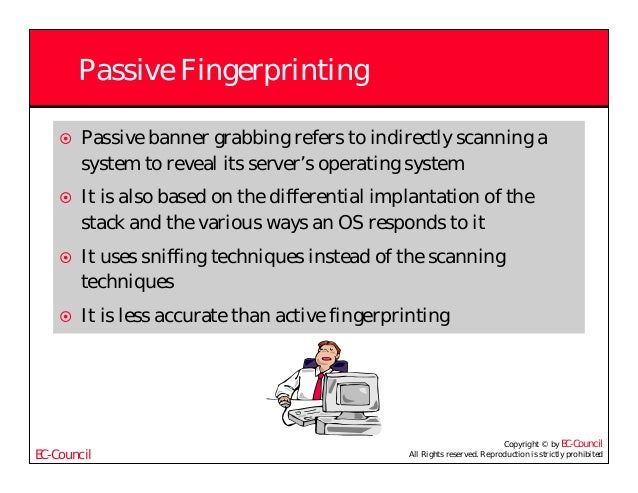
The problem with both ettercap and p0f is they just do passive tcp fingerprinting.
Banner grabbing is the act of capturing the information provided by banners configurable text based welcome screens from network hosts that generally display system information.
Reading the responses to a connect scan.
I did a paper on this about 12 18 months ago.
Many services will respond with a simple text message known as a service banner indicating the technology in use.
The first 11 pages out of about 50 are on active fingerprinting.
Banner grabbing is a process to collect details regarding any remote pc on a network and the services running on its open portsan attacker can make use of banner grabbing in order to discover network hosts and running services with their.
Banner grabbing and operating system identificationwhich can also be defined as fingerprinting the tcpip stackis the fourth step in the ceh scanning methodologythe process of fingerprinting allows the hacker to identify particularly vulnerable or high value targets on the network.
Banner grabbing is a reconnaissance technique to discover network services by simply querying the service port.

Types Of Reconnaissance Active And Passive Getting Started
Endpoint Protection Symantec Enterprise

Presenter Bio Strengths Weakness Security Interests Something Fun

Binary Logit Analysis For Passive Ad Banner Click Response Note
The Seven Step Information Gathering Process Footprinting And
Ethical Hacker Net Blog A Security Driven Knowledge Defeating
Solved If Someone Could Please Help Me And Explin This St

Seguridad Ofensiva Os Fingerprinting A Brief History

Banner Grabbing

Penetration Testing Intelligence Gathering

Change Passive Voice To Active Voice Active Voice Academic

The Seven Step Information Gathering Process Footprinting And

Seguridad Ofensiva Os Fingerprinting A Brief History

Seguridad Ofensiva Os Fingerprinting A Brief History
Ceh V5 Module 03 Scanning

Ethical Hacking Scanning Networks

Banner Grabbing With Netcat Sciencedirect
The Hacker S Guide To Website Security Page 2 Techradar

Characterization Of A Very Large Iot Probing Campaign C15 Of

Pdf New Tool And Technique For Remote Operating System

Free Issuu Pdf Download Tool Online Vebuka Com

Certified Ethical Hacker Ceh Version 9 Cert Guide 2nd Edition

Best Banner Grabbing Tools For Ethical Hacking Latest Hacking
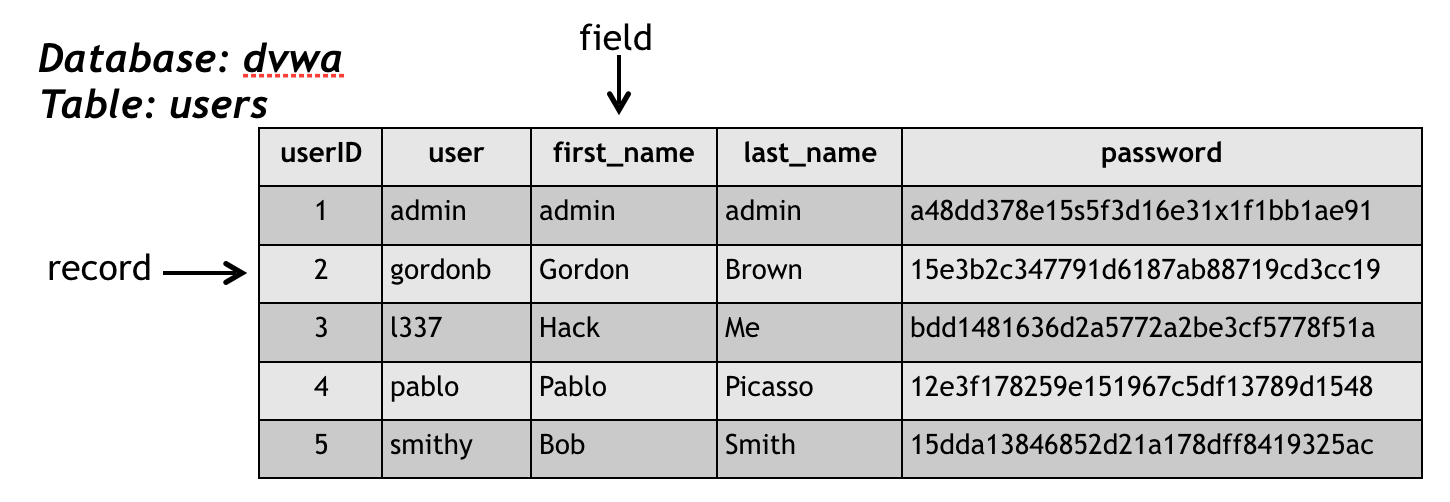
Hacking And Your Cybersecurity Future

Https Www Mdpi Com 2073 8994 10 5 151 Pdf

Cybersecurity Fingerprinting What Is It Fingerprint Techniques

Banner Grabbing

Foot Printing Scanning Tools Lect 4 Netw Ppt Download

How To Write Attention Grabbing Sentences Active Vs Passive

Banner Grabbing With Netcat Sciencedirect

Http Lpc1 Clpccd Cc Ca Us Lpc Mdaoud Cnt7501 Netlabs Ethical Hacking Lab 02 Pdf

Hacking And Your Cybersecurity Future

Unicornscan Kali Linux Reconnaissance Phase Youtube

Foot Printing Scanning Tools Lect 4 Netw Ppt Download
Active And Passive Information Gathering Techniques Part 3

Endpoint Protection Symantec Enterprise

Pentesting Methodology 101

Ec Council Certified Ethical Hacker Version 6 Pdf Free Download

Port Scanners

Banner Grabbing With Netcat Sciencedirect
Active And Passive Information Gathering Techniques Part 3

How To Banner Grabbing With Netcat

Mod 3 Part I Pages 1 3 Text Version Anyflip

Host Scanner Active Passive Network Scanner And Autonomous

Life Beyond Nmap Ptlabs

9 Ethical Hacking Passive Vs Active Footprinting Youtube

Elearnsecurity Vs Oscp The Norseman

Best Banner Grabbing Tools For Ethical Hacking Latest Hacking

Evapi Enumeration Auburn Hacking Club Ppt Download

Oscilloscope Passive Active Probes Explained Warwick Test Supplies

15 Most Useful Host Scanning Commands Kali Linux Yeah Hub

Inferring And Mitigating Internet Scale Unsolicited Iot Devices A
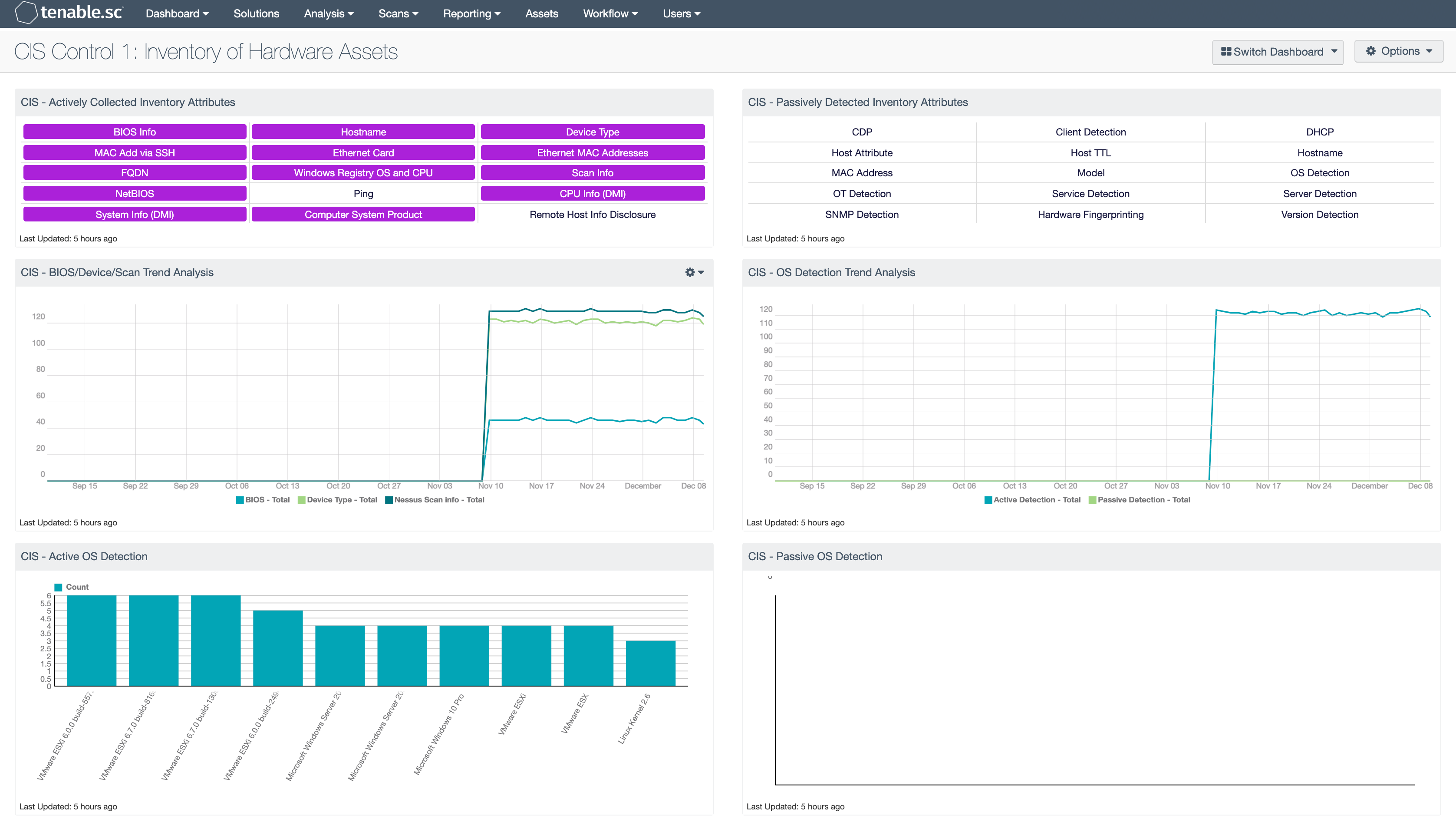
Cis Control 1 Inventory Of Hardware Assets Sc Dashboard Tenable

Anatomy Of The Hack Hands On Security Information Assurance Club

40 Cyber Security Mcq With Answers And Explanations Yeah Hub
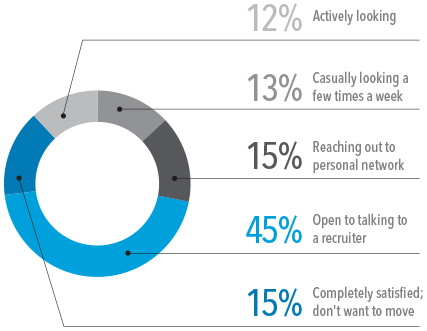
Active Vs Passive Candidates The Latest Global Breakdown

Banner Grabbing With Netcat Sciencedirect
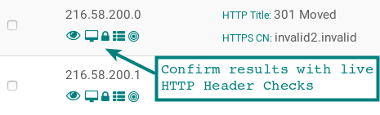
Banner Grabbing Search

Unicornscan Port Scanning Tutorial Hackersploit Infosec

Best Banner Grabbing Tools For Ethical Hacking Latest Hacking

Ppt Network Reconnaissance And Enumeration Powerpoint

Http Lpc1 Clpccd Cc Ca Us Lpc Mdaoud Cnt7501 Netlabs Ethical Hacking Lab 02 Pdf

The Best Gaming Mouse For Any Budget In 2020 Wired Uk

Ppt Network Mapping Powerpoint Presentation Free Download Id

Banner Grabbing Search

Https Www Mdpi Com 2073 8994 10 5 151 Pdf

Ppt Itt Certified Ethical Hacker Certification Study Group

Http Lpc1 Clpccd Cc Ca Us Lpc Mdaoud Cnt7501 Netlabs Ethical Hacking Lab 02 Pdf

Learn Web Application Penetration Testing Noteworthy The

Hacking And Your Cybersecurity Future
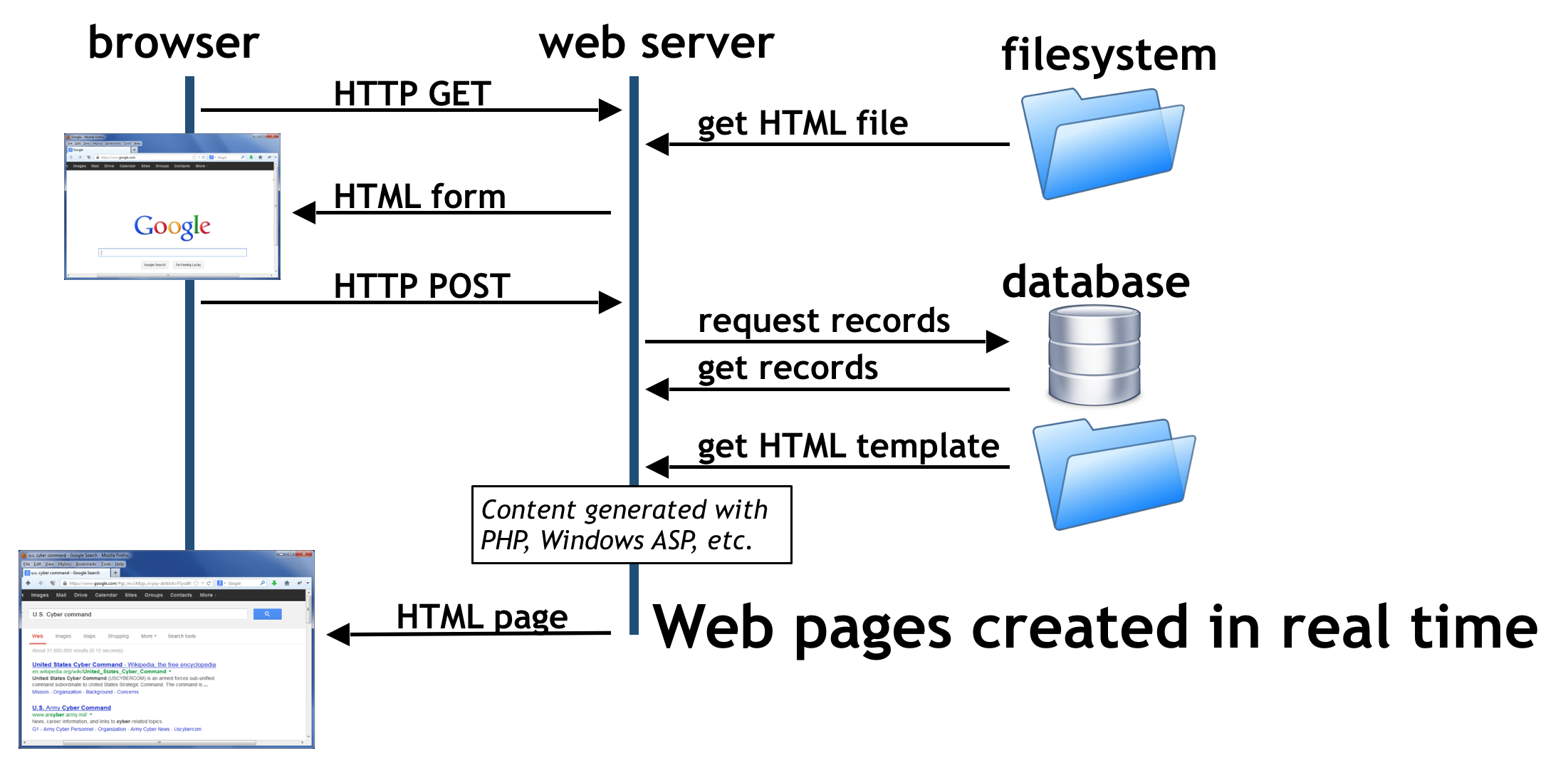
Hacking And Your Cybersecurity Future

Pdf Internet Of Malicious Things Correlating Active And Passive

Cehv9 Module 03 Scanning Networks 1
Active And Passive Information Gathering Techniques Part 3
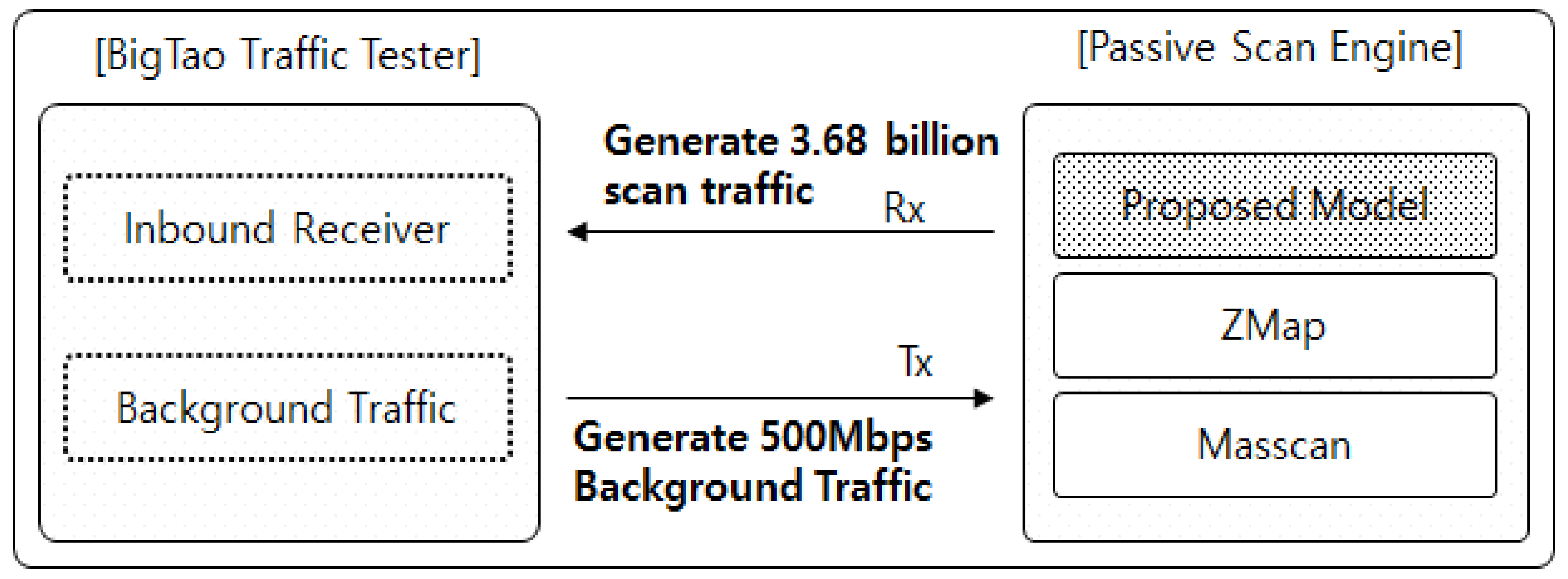
Symmetry Free Full Text An Intelligent Improvement Of Internet

Penetration Testing Services In Dubai Penetration Testing In Dubai

What Is Banner Grabbing Best Tools And Techniques Explained

Ftp Penetration Testing Briskinfosec

Banner Grabbing With Netcat Sciencedirect
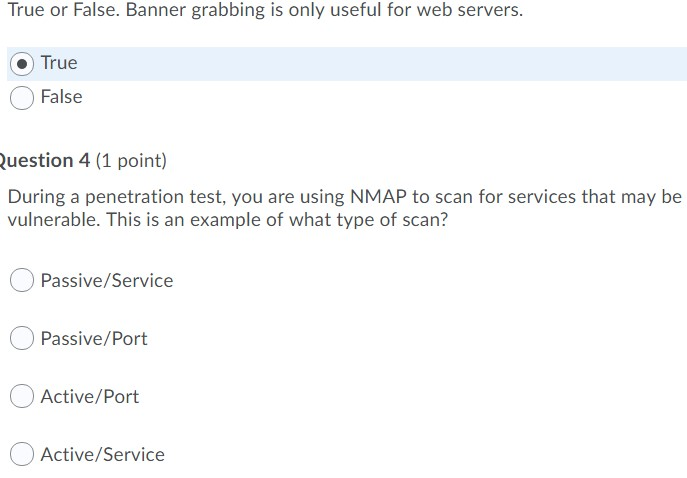
True Or False Banner Grabbing Is Only Useful For Chegg Com

Ethical Hacking Tools Information Grathring
Active And Passive Information Gathering Techniques Part 3

Hacking
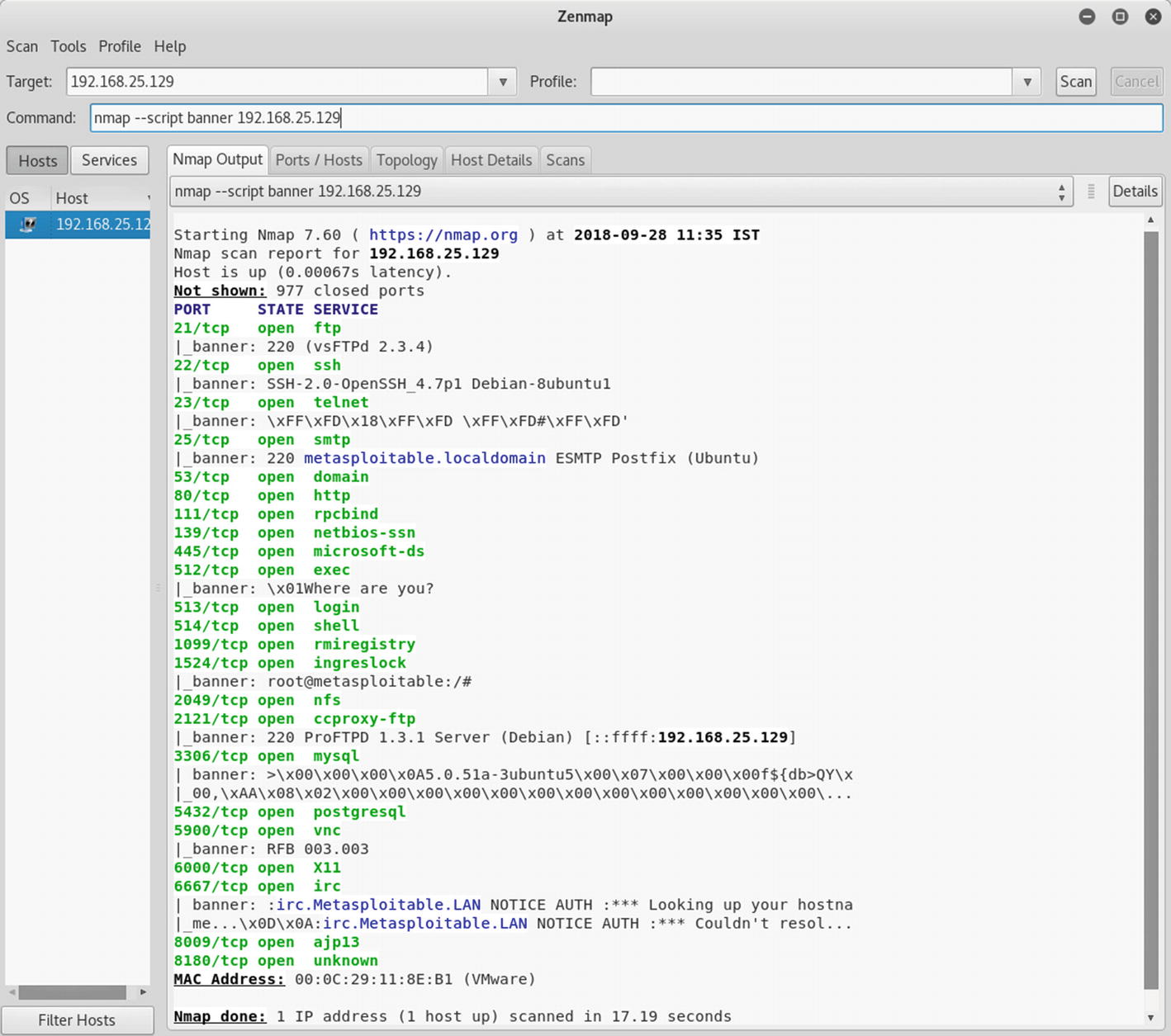
Introduction To Nmap Springerlink
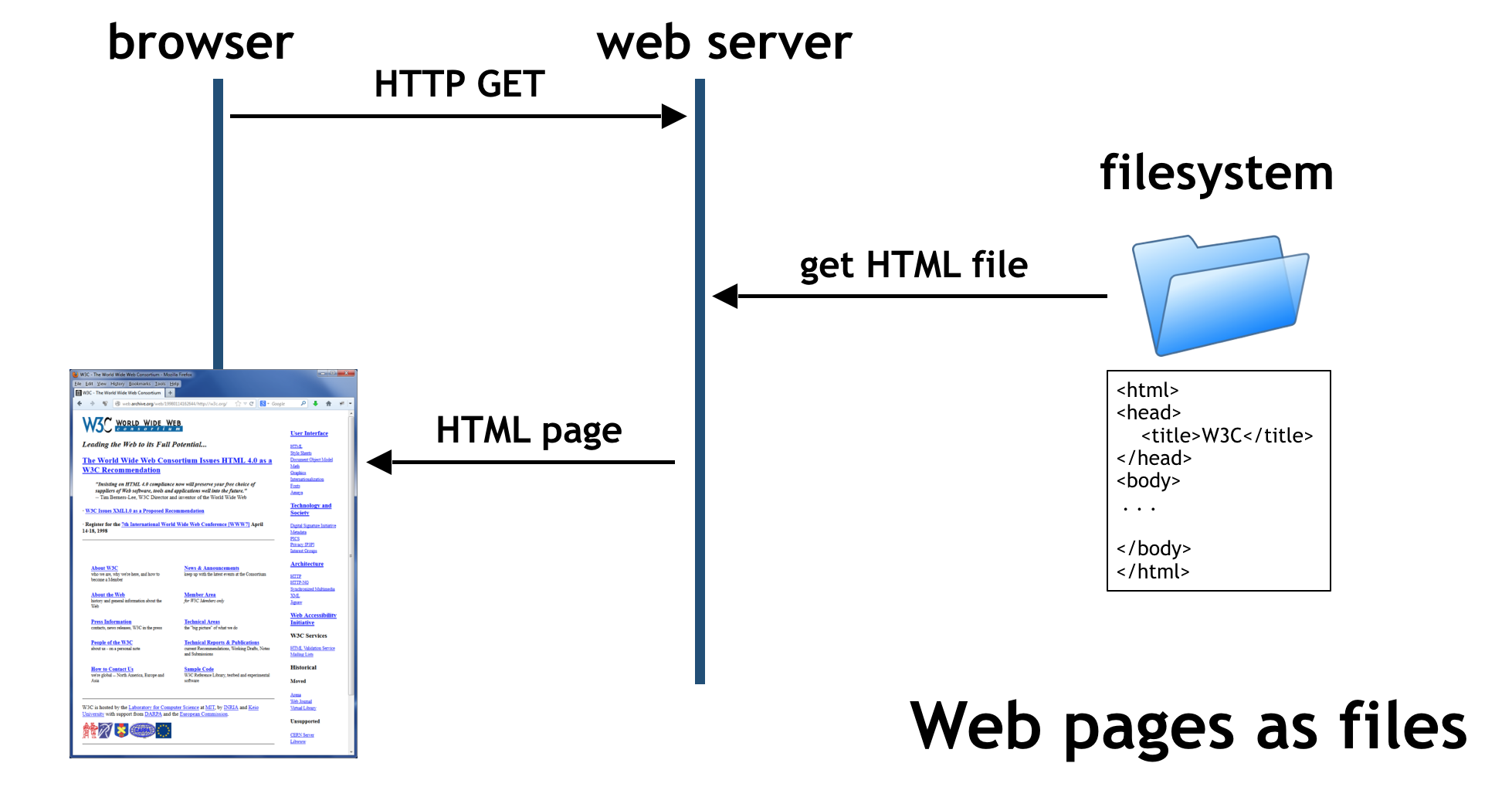
Hacking And Your Cybersecurity Future

What Is Banner Grabbing Best Tools And Techniques Explained

Banner Grabbing
Seguridad Ofensiva Os Fingerprinting A Brief History

Easy Hacker Chapter 03 Scanning Networks
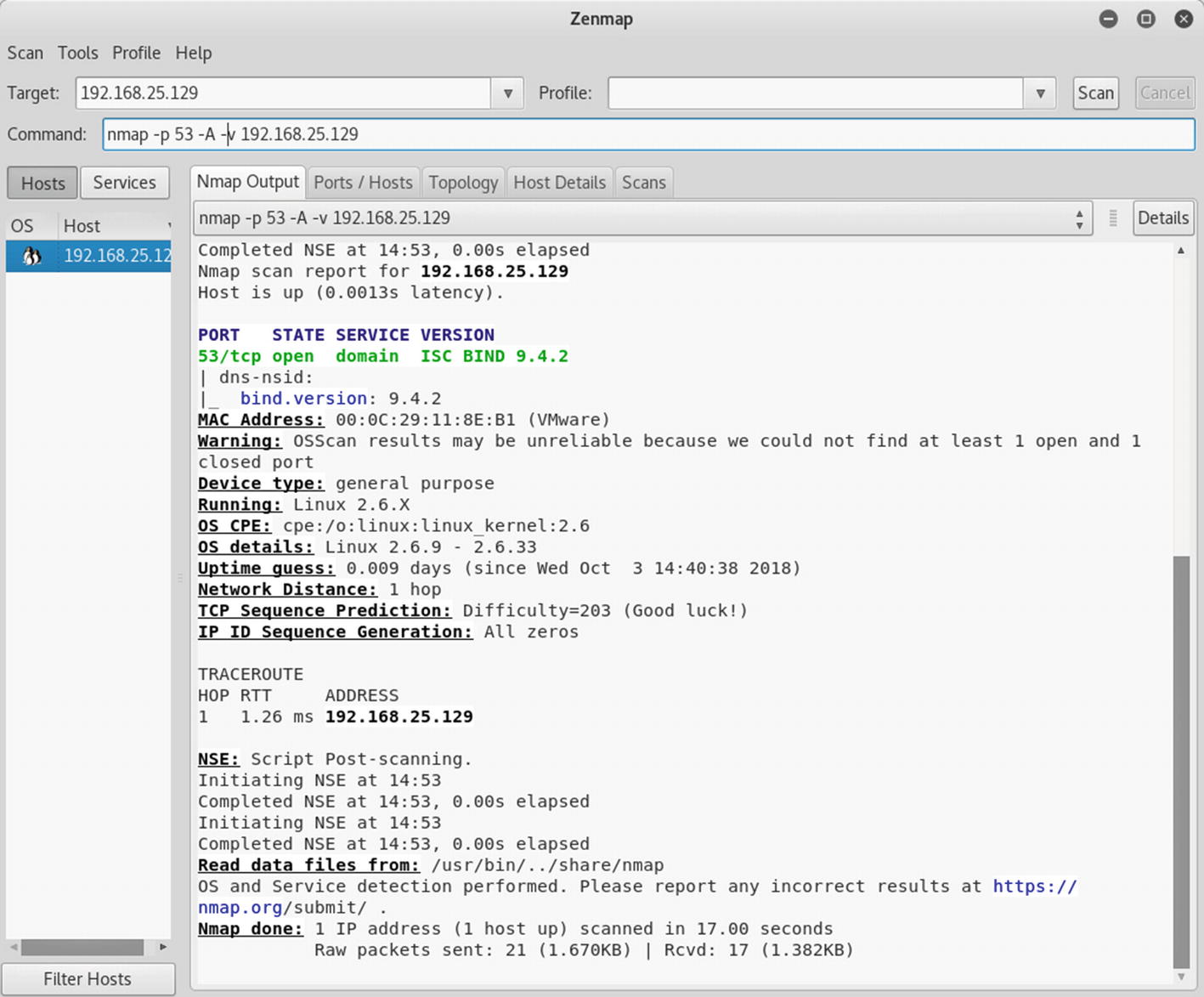
Introduction To Nmap Springerlink
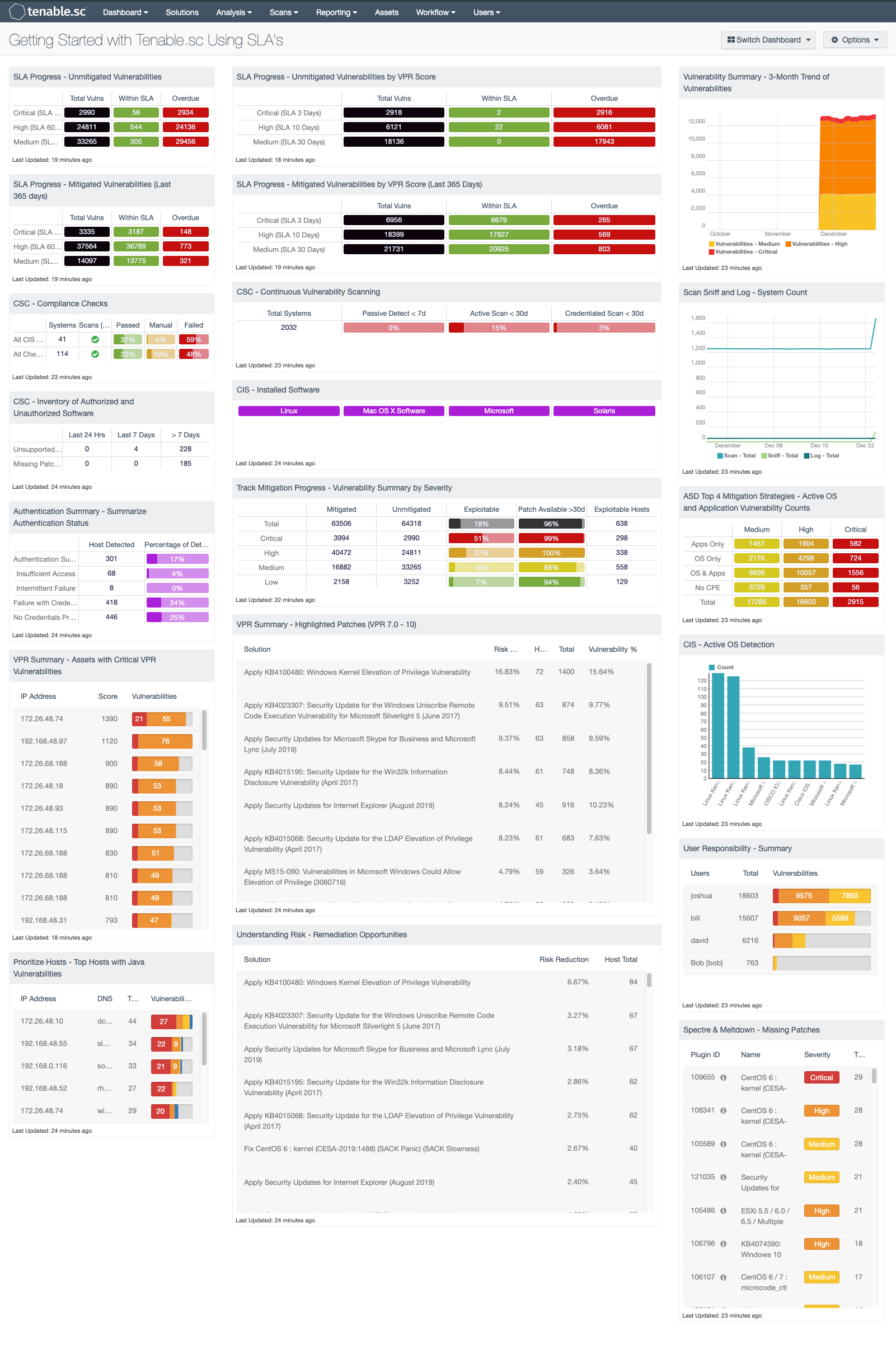
Getting Started With Tenable Sc Using Sla S Sc Dashboard Tenable

Penetration Testing Intelligence Gathering

Cyber Security And Ethical Hacking Mcq With Answers Part 1

Process Scanning And Enumeration

Ethical Hacking Course

Easy Hacker Chapter 03 Scanning Networks
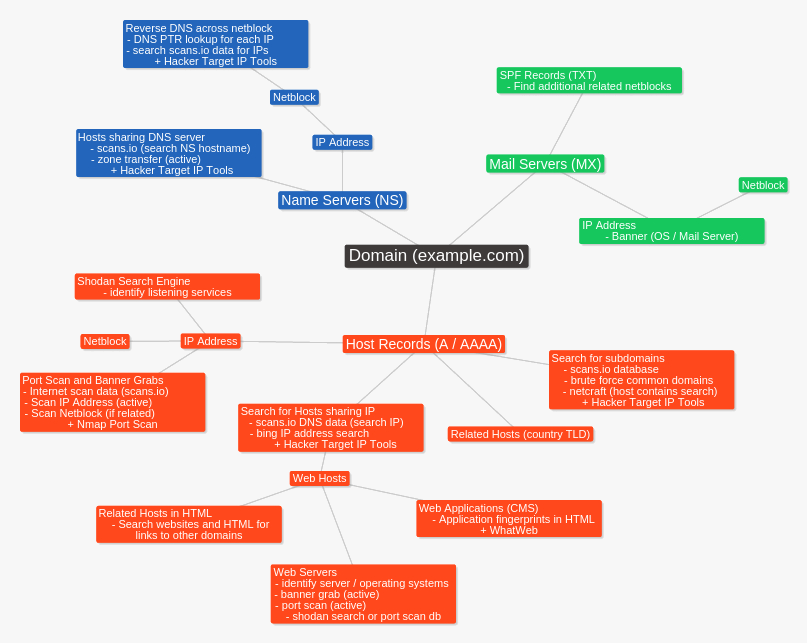
Quietly Mapping The Network Attack Surface

Figure 6 From New Tool And Technique For Remote Operating System